Cloud-Native Data Protection
Leaders Acronis, Commvault, Veritas, Druva and HYCU
This is a Press Release edited by StorageNewsletter.com on August 16, 2024 at 2:02 pm![]() This market report, published on August 7, 2024, was written by Chester Conforte, author at GigaOm.
This market report, published on August 7, 2024, was written by Chester Conforte, author at GigaOm.
GigaOm Sonar for Cloud-Native Data Protectionv2.0
An Exploration of Cutting-Edge Solutions and Technologies
1. Executive Summary
Many organizations are investing heavily in the cloud to improve their agility and optimize the TCO of their infrastructure. They are moving applications and data to the public cloud to take advantage of its flexibility only to discover that, when not properly managed, public cloud costs can quickly spiral out of control. This can leave them exposed to unintentional risk due to their lack of experience managing diverse shared-responsibility models.
Storage and protection are among the biggest pain points along many cloud adoption journeys. Many of the services available in a cloud need to be enhanced and hardened to deliver the predictable reliability and availability of more traditional enterprise technology architectures. The tools for managing the protection of data, state, and configuration saved in those systems must operate well beyond simple snapshot-based data protection.
In addition, organizations are taking advantage of the flexibility and broad set of offerings provided by public clouds. It is not uncommon for an organization to consume cloud services from different public cloud providers. In that context, multicloud support and the ability to abstract management complexities behind a unified management pane drastically simplify data protection operations and increase operational efficiency.
Cloud-native data protection solutions are designed to add enterprise-class data protection functionality that leverages modern cloud patterns of infinitely scalable storage, microservices, containerization, functions, automation, orchestration capabilities, and DevOps practices. These features enable greater scalability, resilience, and agility compared to traditional monolithic appliance, virtual, or cloud-hosted applications while improving data management processes and costs.
Compared to traditional backup solutions, cloud-native data protection offers several advantages by streamlining operations, minimizing duplication of infrastructure costs and effort, and leveraging investments in cloud adoption to more tightly align with a business’s strategic digital transformation objectives.
In this regard, organizations should take into account some important factors of cloud-native data protection solutions:
- Speed: When properly integrated, cloud-native backup can take advantage of the underlying cloud’s elasticity, scalability, and competitive differentiators to speed up backup and restore operations. It’s not uncommon for cloud-native backup solutions to blur the lines between data protection, cyber security, and business continuity. This hybridization has the intended consequence of delivering supreme levels of resilience and business agility in a continuously evolving cyber landscape.
- Granularity: One of the biggest limitations of traditional backups is the inability to easily restore the “what, when, and how it was” in the event of a data loss incident. To do this, users typically have to go through layers of people, processes, and technology inefficiencies to find, restore, and recover data to a known good state – often leaving teams to hunt and peck for nuggets of data using coarse-grained tools. This slow and error-prone process bleeds a business’s velocity and ultimately impacts its ability to maintain high levels of execution and momentum.
- Cyber resiliency: Creating distance between source and backup targets is the basis of every safety and security practice in data protection, especially with the increasing number of cyber-attacks becoming the norm. The 3-2-1 principle, originating from the era of on-premises data storage, remains a widely referenced guideline in modern data protection. This well-established principle can still serve as a valuable framework for business and security decision-makers for enhancing their cyber infrastructure against contemporary data risks. In essence, the 3-2-1 backup rule advocates for maintaining three copies of data across two distinct storage media types, with one copy stored off-site. Data immutability, air gapping, security scanning, and proactive remediation are foundational capabilities for hedging against a worsening security and compliance threat landscape. The ultimate objective of a cloud-native backup solution is the peace of mind that comes from knowing that when (not if) a loss event occurs, your data is protected.
- Cost: Often delivered within a SaaS model, cloud-native data protection solutions provide a similar pay-as-you-grow approach through which the organization can immediately reap the benefits of data protection while either owning the orchestration of managing the data protection infrastructure or transferring the difficulties to the software provider. Unlike traditional big iron deployments or virtualized software approaches, customers do not need to handle the costs associated with over-architecting monolithic solutions for corner case scenarios. Cloud-native data protection solutions offer a more agile and dynamic approach to selectively scaling and balancing innovation, maturity, use, and cost for its consumer base.
For this report, we focused on cloud-native data protection tools and did not include on-premises vendors previously covered in GigaOm’s Radar reports on hybrid cloud data protection (HCDP) for SMBs and large enterprises. Among the criteria for inclusion, we looked at both SaaS and pure-play software providers built with modern cloud principles (such as microservices or a serverless architecture) and using scalable storage paradigms. We also looked at each solution’s ability to predominantly protect SaaS, hyperscaler-native, and private cloud workloads while not abandoning traditional endpoint and enterprise workloads, ideally in multicloud scenarios. Finally, we also looked at solutions that offer seamless, cloud-like consumption models, offering pay-as-you-grow economics coupled with elastic scalability.
This is the second year that GigaOm has reported on the cloud-native data protection space in the context of our Sonar reports. This report builds on our previous analysis and considers how the market has evolved over the last year.
This Sonar report provides an overview of the market’s vendors and their available offerings, outlines the key characteristics that prospective buyers should consider when evaluating solutions, and equips IT decision-makers with the information they need to select the best solution for their business and use case requirements.
2. Overview
As the adoption of public cloud services continues to soar, the demand for cloud-native data protection solutions has followed a similar trajectory. Initially, organizations leveraged the public cloud for lift-and-shift operations, allowing them to use traditional on-premises data protection solutions without major modifications. However, the gradual shift toward cloud-native services and containers eventually rendered these traditional solutions impractical. Compounding this challenge, an increasing number of mission-critical applications are now running in the cloud, heightening the need for robust and scalable data protection strategies.
The public cloud infrastructure itself provides a comprehensive toolbox for designing resilient and scalable data protection solutions. Containers, serverless functions, native snapshot capabilities, and immutable object storage available in multiple tiers and flavors serve as foundational components of cloud-native data protection solutions. These building blocks enable data protection vendors to construct robust services with increased added value for their customers.
One of the key advantages of cloud-native data protection solutions lies in their ability to leverage availability zones and geographically distributed regions. By spreading the infrastructure backend across both logical and physical space, vendors can enhance the resilience of their solutions vs. potential failures. Furthermore, regions and availability zones offer a valuable opportunity to increase the protection of customer data. Data at rest can be durable when spread across multiple boundaries, ensuring recoverability in the event of either intentional or unintentional primary data loss.
Moreover, cross-boundary data durability can be coupled with cross-cloud availability, providing an additional layer of assurance. In this scenario, the secondary data copy is stored on a different account or on a different cloud, preventing data loss if the primary cloud used to store the data has become unavailable.
The nature of cloud-native data protection solutions and their architecture lends itself to a service-based delivery model, abstracting the back-end complexity and delivering immediate value to enterprises seeking a more resilient approach to data protection. Just as organizations expect to spin up workloads and services within minutes, they rightfully expect to protect their data and workloads with the same or even greater efficiency.
This delivery model also implies a shift in consumption models and pricing. Rather than consuming data protection services through a capacity-based subscription license or a fixed, CapEx-based per-server set of licenses, cloud-native data protection solutions offer flexibility and operate using a pay-as-you-go model, often based on consumed capacity. In certain cases, the data processing back-end of the solution itself also scales to adapt to the changing needs of the organization, leading to cost savings regardless of whether part of the cloud-native data protection solution is operated by the customer or the solution provider. For example, some solutions take advantage of ultra-low cost, unreliable, and ephemeral “spot” compute instances by design.
Another crucial cost aspect to consider is storage. Some solutions include storage costs in the bill, while others operate under a bring-your-own-storage (BYOS) model or a mix of both. Under a BYOS model, the customer is responsible for providing the cloud-native storage and will be charged for using it by their storage provider. Consequently, it is essential to have a thorough understanding of the pricing characteristics of each solution to make informed decisions that take into account future growth trends.
As organizations continue to embrace cloud-native paradigms, the demand for cloud-native backup technologies will only intensify. These solutions offer a compelling value proposition, leveraging the inherent advantages of cloud infrastructure to deliver resilient, scalable, and cost-effective data protection services. By abstracting the complexities of the back end and providing a seamless, service-based delivery model, cloud-native backup technologies empower enterprises to safeguard their mission-critical data with the same agility and simplicity they have come to expect from the cloud.
3. Considerations for Adoption
Market Categories
To help prospective customers find the best fit for their use case and business requirements, we assess how well cloud-native data protection solutions are designed to serve specific target markets (Table 1). All the solutions included in this report are deployed via software as a service (SaaS), and so we’re not evaluating deployment models for this sector.
For this report, we recognize the following market segments:
- CSP: The CSP market – led by AWS, Azure, and Google Cloud – emphasizes certifications, data security, service reliability, and cost efficiency. Purchase considerations include SLAs, compliance, support, and pricing models. Buyers range from transformational to price-conscious, focusing on scalability, security, and cost management.
- Network service provider (NSP): The NSP market – led by telecom, MSO, and mobile operators – emphasizes the need for efficient network management, enhanced security, and scalability. Buyer requirements include compatibility with existing infrastructure, technical expertise, and budget considerations. Purchase decisions focus on SLAs, support, and pricing models. Buyers range from enterprises seeking robust, scalable solutions to those looking to drive cost-effective, streamlined network management.
- MSP: MSPs operate in a dynamic segment characterized by disaggregated, open-standards-based technology stacks that promote interoperability. Buyers prioritize scalability, performance, and TCO when selecting MSP solutions. Key purchase considerations include the ability to customize and integrate various hardware and software components, ensuring seamless operations and reducing risk exposure. MSPs must also support emerging technologies like AI, AR, and ML to meet evolving enterprise needs.
- SMB: SMBs require solutions that are easy to use, cost-effective, and scalable. This market segment includes diverse organizations with varying IT budgets and needs. Key buyer requirements include data protection for hybrid and cloud workloads, seamless integration with existing systems, and flexible deployment options. Purchase considerations focus on pricing transparency, ease of deployment, and the ability to support core business functions without extensive customization.
- Large enterprise: Large enterprises require solutions that support large-scale, business-critical projects with a focus on flexibility, performance, data services, security, and data protection. Scalability and the ability to deploy services in different environments are crucial. Purchase considerations include the solution’s ability to integrate with existing systems, comprehensive coverage across various domains, and robust integration capabilities.
- Multinational: A multinational enterprise in the emerging technology market segment prioritizes scalability, flexibility, and integration with existing enterprise tools. Buyer requirements include robust feature sets, seamless integration with IT and security systems, and the ability to support large, business-critical projects. Purchase considerations focus on the balance among cost, advanced capabilities, and regulatory compliance.
Table 1. Vendor Positioning: Target Market
Table 1 components are evaluated in a binary yes/no manner and do not factor into a vendor’s designation as a Leader, Challenger, or Entrant on the Sonar chart (Figure 1).
“Target market” reflects which use cases each solution is recommended for, not simply whether that group can use it. For example, if an SMB could use a solution but doing so would be cost-prohibitive, that solution would be rated ‘no’ for SMBs.
Key Characteristics
Here we explore the key characteristics that may influence enterprise adoption of the technology, based on attributes or capabilities that may be offered by some vendors but not others. These criteria will be the basis on which organizations decide which solutions to adopt for their particular needs.
The key characteristics for cloud-native data protection solutions are:
- Cloud-native data plane (CNDP) architecture
- Management plane durability
- Retention and recoverability
- End-to-end encryption (E2EE)
- Granularity
- Data movement optimization
- Data management and analytics
- Storage capacity efficiency
- Cyber resilience
- Diverse data sources
- CNDP Architecture
The CNDP architecture optimizes storage and processing for cloud-native applications, leveraging modern well-architected cloud principles for unmatched scalability, resilience, and agility.
It employs infinitely scalable storage, microservices, containerization, and orchestration. By breaking down applications into microservices, each component can be independently developed, deployed, and scaled. Containerization ensures a consistent runtime environment, enhancing portability and simplifying deployment. Orchestration tools like Kubernetes automate container management, ensuring efficient resource use and high availability. DevOps practices, including continuous integration/continuous deployment (CI/CD), streamline development and deployment, enabling rapid innovation.
CNDP supports dynamic and ephemeral scaling, allowing services to adjust in real time based on demand. This elasticity ensures efficient resource utilization and cost reduction. Ephemeral environments, created on-demand, facilitate comprehensive testing and rapid deployment, enhancing system agility and responsiveness, especially during peak loads.
By leveraging multicloud infrastructure, CNDP enhances service delivery through the best features of various cloud providers. This strategy mitigates vendor lock-in risks and ensures high availability and fault tolerance. Distributing workloads across multiple clouds provides seamless failover capabilities, reducing outage impacts and ensuring continuous service delivery. Multicloud deployments also help to achieve compliance with regional regulations and optimize performance by selecting the most suitable cloud services for specific tasks.
In summary, CNDP architecture harnesses cloud-native technologies, dynamic scaling, and multicloud infrastructure to deliver robust, elastic, and agile data processing solutions.
Management Plane Durability
Management plane service durability is a critical aspect of cloud-native backup technologies, ensuring the resilience and reliability of backup operations. The durability of the management plane across clouds and providers is crucial for robust, resilient, and reliable cloud-native backup solutions.
In a single data center or cloud region, the management plane must ensure high availability and fault tolerance. This involves deploying redundant systems and leveraging robust infrastructure to mitigate risks associated with localized failures. For instance, Amazon Web Services (AWS) and Google Cloud Platform (GCP) offer services that maintain high availability within a single region by using multiple availability zones, which are isolated data centers within the same region. This setup ensures that even if one zone fails, the management plane can continue to operate seamlessly, providing uninterrupted backup and recovery services.
Expanding availability across geo-distributed regions within a single cloud provider enhances resilience against regional outages. Cloud providers like AWS, GCP, and Azure offer multiregion deployments that replicate data and services across different geographic locations. This geo-distribution ensures that if an entire region goes offline due to a natural disaster or other catastrophic event, the management plane can still function by switching operations to another region. This approach significantly reduces downtime and ensures business continuity.
The ultimate in management plane durability is achieved through availability across multiple cloud providers. This cross-cloud strategy involves using a unified console to manage backups and recoveries across different cloud environments, such as AWS, Azure, and GCP. This approach mitigates the risk of vendor lock-in and also enhances resilience by distributing workloads and data across diverse platforms. Tools like AWS Systems Manager and Azure Arc facilitate this resilience by providing centralized management and governance, ensuring consistent security, compliance, and operational efficiency across multicloud environments.
Retention and Recoverability
Cloud-native backup technologies are changing data protection by offering robust retention and recoverability features that are essential for business continuity. These characteristics collectively ensure that cloud-native backup technologies provide a comprehensive, scalable, and secure approach to data retention and recoverability, supporting uninterrupted business operations.
One of the key characteristics is the ability to perform point-in-time scheduled restores. This feature allows organizations to recover data from any specific point within a retention period, typically up to one year. This capability is crucial for mitigating data loss from accidental deletions, corruption, or cyber-attacks, ensuring that businesses can revert to a precise moment in time to restore their operations seamlessly.
Infinite retention is another significant feature, allowing organizations to store an unlimited amount of data without time restrictions. This is particularly beneficial for industries such as finance and healthcare that operate under stringent regulatory requirements mandating that data be retained for extended periods. Infinite retention simplifies data management by eliminating the need for periodic data purging and ensuring that historical data is always accessible.
Access to provider-managed cloud resources is vital for business continuity. Cloud-native backup solutions leverage the scalability and resilience of cloud infrastructure, providing continuous data protection and rapid recovery capabilities. This access to resources ensures that businesses can maintain operations with minimal downtime, even in the face of disasters. The cloud’s inherent redundancy and security features further enhance data protection, making it a reliable choice for safeguarding critical business information.
E2EE
It is a critical feature in cloud-native backup technologies, ensuring data security throughout its lifecycle. These characteristics collectively ensure robust data protection, compliance, and control in cloud-native backup solutions.
E2EE ensures that data is encrypted both while being transmitted (in transit) and when stored (at rest). Encryption in transit protects data from interception during transit over networks, using protocols like TLS to secure the connection. Once data reaches its destination, encryption at rest safeguards it from unauthorized access, ensuring that even if storage media are compromised, the data remains unreadable without the decryption key. This dual-layer protection is essential for maintaining data confidentiality and integrity in cloud environments.
Client-side encryption involves encrypting data at the source before it is sent to the cloud. This method ensures that data is protected from the moment it leaves the client’s environment, preventing exposure to any third parties, including the cloud service provider.
Bring your own key (BYOK) allows organizations to use their own encryption keys rather than relying on keys provided by the cloud service provider. This approach enhances control over data security and compliance with regulatory requirements. Additionally, key rotation, which involves periodically updating encryption keys, is crucial for maintaining security hygiene: ensuring that encryption keys are regularly updated to mitigate risks associated with key compromise.
Granularity
It is a critical characteristic of cloud-native backup technologies, enabling precise and efficient data recovery. Granularity in cloud-native backup technologies enhances the precision and efficiency of data recovery across various storage types, instances, and configurations, ensuring robust data protection and minimal operational downtime.
Granular recovery in file and object storage allows for the restoration of specific files or objects without needing to recover entire datasets. This is essential for endpoints, sync-and-share services and file stores, from which users often need to retrieve individual files quickly.
For metal instances, VMs, containers, and application data, granular recovery ensures that specific components can be restored without affecting the entire system. This is crucial for maintaining the performance and availability of critical applications and databases. For these datasets, the solution should allow administrators to restore individual VMs, containers, or application records, ensuring minimal disruption to operations.
Granular recovery extends to cloud account configurations, enabling the restoration of specific settings and policies in public or private IaaS or PaaS environments. This restoration of settings is vital for maintaining the integrity and security of cloud infrastructures. A cloud-native solution should provide tools to recover specific configurations, ensuring that cloud environments can be quickly and accurately restored to their desired state after a disruption.
Data Movement Optimization
It is crucial for enhancing the efficiency and performance of cloud-native backup technologies, ensuring data is protected and readily accessible as quickly as possible.
Effective bandwidth management is essential for optimizing data movement. It involves regulating the amount of data transferred over a network to prevent congestion and ensure critical applications receive the necessary bandwidth. Techniques such as data compression, de-dupe, and traffic shaping help reduce the volume of data traversing the network, thereby improving transfer speeds and reducing latency. By prioritizing essential data and managing bandwidth allocation, organizations can maintain high performance and reliability in their backup processes.
Using private links and software-defined wide area network (SD-WAN) technologies can significantly enhance data movement by providing more efficient and reliable network paths. SD-WAN offers intelligent traffic routing and path selection, optimizing the use of available bandwidth and reducing latency. Additionally, caching capabilities store frequently accessed data locally, minimizing the need for repeated data transfers and further improving network efficiency. These technologies collectively ensure that data is moved swiftly and securely, supporting robust cloud-native backup solutions.
Cloud seeding is a technique used to expedite the initial data transfer to the cloud. By physically shipping storage devices containing large datasets to the cloud provider, organizations can bypass the limitations of network bandwidth for the initial data load. This method is particularly beneficial for large-scale data migrations, reducing the time required to move data to the cloud and enabling quicker access to cloud-native backup services. Once the initial seeding is complete, incremental updates can be managed more efficiently over the network.
Data Management and Analytics
They are critical components in modern business operations, enabling organizations to harness the power of their data for strategic decision-making. Robust data management and analytics systems provide the tools needed for effective data visualization, compliance, and strategic financial planning.
Dashboards are essential for visualizing key metrics and performance indicators in real time, providing a comprehensive overview of business operations. They facilitate quick decision-making by presenting data in an intuitive format, often through charts and graphs. Batch reporting, on the other hand, involves processing large volumes of data at scheduled intervals, which is crucial for generating comprehensive reports that inform business intelligence and compliance needs. Regulatory reporting ensures that data management practices comply with legal standards, such as GDPR and CCPA, safeguarding data integrity and security.
Effective data management systems must support global indexing and search capabilities, allowing for efficient retrieval of information across vast datasets. E-Discovery, the process of identifying and delivering electronic information for legal proceedings, relies heavily on these capabilities to ensure that relevant data can be located and analyzed quickly. This is particularly important in legal and compliance contexts where timely access to accurate data is critical.
FinOps, or financial operations, integrates financial management with operational practices to optimize cloud spending and improve financial accountability. Predictive analytics leverages historical data to forecast future trends, enabling proactive decision-making and strategic planning. By combining FinOps with predictive analytics, organizations can better manage their resources, reduce costs, and enhance their financial performance through data-driven insights.
Storage Capacity Efficiency
It is a critical aspect of cloud-native backup technologies, ensuring optimal use of storage resources and cost-effectiveness. Three key characteristics that enhance storage capacity efficiency are source-side compression/de-dupe, target-side compression/de-dupe, and global compression/de-dupe. Together, these techniques ensure that cloud-native backup solutions maximize storage capacity efficiency, providing scalable, cost-effective, and reliable data protection.
Source-side compression/de-dupe occurs at the data’s origin, reducing the volume of data before it is transferred over the network. By eliminating redundant data blocks at the source, it minimizes network traffic and accelerates backup windows. This method is particularly beneficial for environments with low daily data change rates, such as remote offices and edge devices, as it reduces the need for extensive infrastructure investments.
Target-side compression/de-dupe occurs once data reaches the backup target and further compression and de-dupe occur. This method focuses on eliminating redundancies within the stored data vault, significantly reducing storage space requirements. Target-side de-dupe is advantageous because it is backup application agnostic, allowing seamless integration with existing backup workflows without major modifications.
Global compression/de-dupe extends de-dupe and compression across multiple datasets and storage locations, ensuring that only unique data blocks are stored globally. By leveraging a single, scale-out repository, global de-dupe optimizes storage efficiency and enhances data management. This method is crucial for organizations with fragmented data across hybrid and multicloud environments, as it consolidates storage assets and reduces overall storage costs.
Cyber Resilience
It ensures that organizations can withstand, recover from, and adapt to cyber attacks and threats. A robust cyber resilience strategy enables organizations to maintain business continuity and protect critical assets in an increasingly hostile cyber environment.
Data immutability is essential for protecting critical data from tampering, modification, or deletion by unauthorized parties. Immutable backups ensure that once data is written, it cannot be altered, providing a reliable recovery point in the event of a cyberattack. This is particularly important in the face of ransomware, by which attackers often target backup data first. By maintaining immutable backups, organizations can ensure that their data remains secure and recoverable, minimizing downtime and financial losses.
Malware discovery and impact analysis involve identifying and understanding malicious software to mitigate its effects. Effective malware analysis can detect indicators of compromise (IoCs), guide incident response teams, and inform remediation strategies. This process helps organizations understand the scope of an attack, prioritize recovery efforts, and improve defenses against future threats. By continuously monitoring and analyzing their backups for malware, organizations can stay ahead of evolving threats and reduce the impact of cyber incidents.
Automated remediation is crucial for responding to cyber threats swiftly and effectively. Automation in cyber-resilient backups allows for real-time detection and response, reducing the time it takes to mitigate threats and recover from attacks. Automated systems can execute predefined actions to isolate affected systems, restore data from immutable backups, and apply necessary patches or updates. This reduces the reliance on manual intervention, minimizes human error, and ensures a faster, more efficient recovery process.
Diverse Data Sources
They are a reality of modern life, so ensuring robust data protection across various environments is an essential characteristic of a good backup solution. By integrating diverse data sources, cloud-native backup technologies ensure comprehensive data protection, operational continuity, and compliance with regulatory requirements.
Cloud-native backup solutions should provide comprehensive protection for endpoints running Windows, Linux, and macOS, as well as native hypervisor workloads like VMware, HyperV, and KVM. These solutions offer scalable and customizable backup options, enabling businesses to protect data from cyber threats, hardware failures, and disasters. A cloud-native endpoint backup solution must support a wide range of devices and operating systems, ensuring business continuity by allowing quick restoration of files and systems.
Cloud-native backup technologies should also support collaborative shared resource targets such as NAS, object storage, and sync-and-share services. They should integrate seamlessly with SaaS applications like Office 365, Salesforce, and Google Workspace, providing automated and secure backups. This integration ensures that critical business data stored in these applications are protected and can be quickly recovered in case of data loss. The solution should offer robust features for managing backups across these diverse environments, enhancing data resilience and operational efficiency.
Cloud-native backup solutions are designed to work seamlessly with leading IaaS and PaaS providers, including OpenStack, AWS, GCP, Azure, and Kubernetes. These solutions should leverage the scalability and flexibility of cloud infrastructure to provide efficient and cost-effective backup services. It should support cross-cloud redundancy, ensuring data integrity and swift recovery across different cloud platforms. The solution should offer centralized management and enhanced data protection across multiple cloud environments.
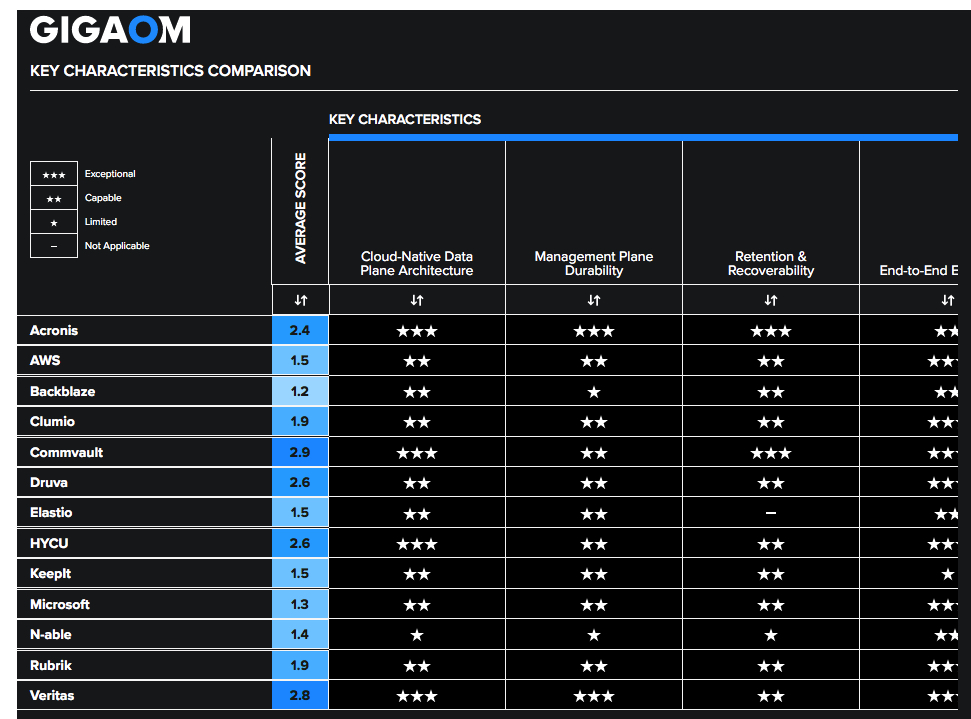
Table 2 shows how well the solutions discussed in this report score in each of these areas.
Table 2. Key Characteristics Comparison

4. GigaOm Sonar
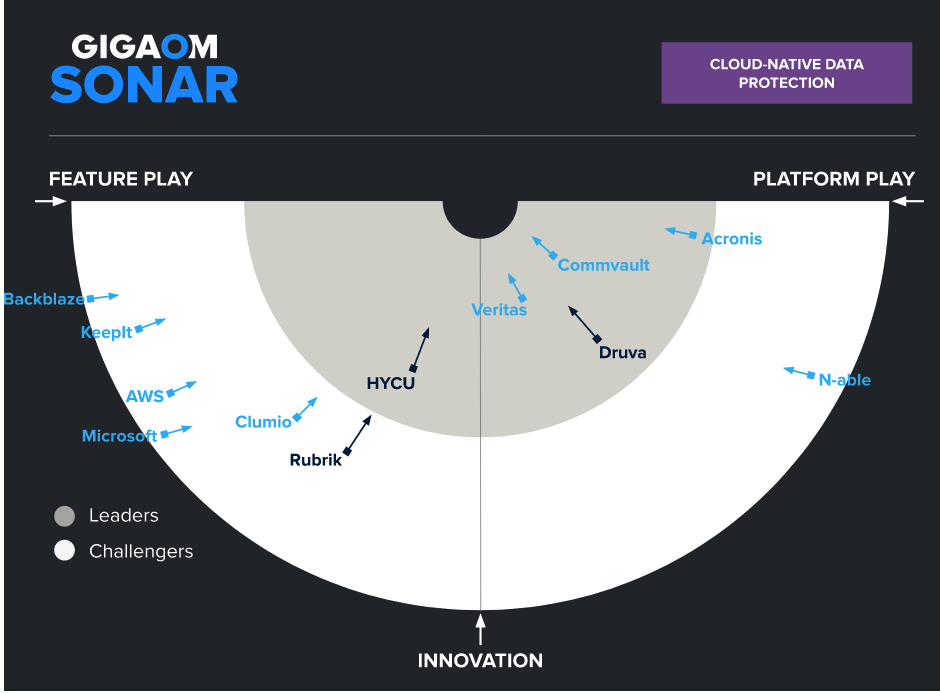
It provides a forward-looking analysis of vendor solutions in a nascent or emerging technology sector. It assesses each vendor on its architecture approach (Innovation), while determining where each solution sits in terms of enabling rapid time to value (Feature Play) versus delivering a complex and robust solution (Platform Play).
The GigaOm Sonar chart (Figure 1) plots the current position of each solution against these three criteria across a field of concentric semicircles, and solutions set closer to the center are judged to be of higher overall value. The forward-looking progress of vendors is further depicted by arrows that show the expected direction of movement over a period of 12 to 18 months.
Figure 1. GigaOm Sonar for Cloud-Native Data Protection
The Sonar chart in Figure 1 categorizes vendors into two main groups: Feature Play and Platform Play. Vendors on the Feature Play side focus on delivering specific, high-performance data protection features tailored to particular needs. These vendors excel in niche areas but may not offer a broad range of capabilities. Examples of specialized features include: air-gapped backups, which provide an isolated backup environment to protect against ransomware, single ecosystem vendor SaaS support like the Microsoft ecosystem of SaaS technologies, and rapid malware detection that ensures minimal impact during a security event.
On the other hand, vendors on the Platform Play side provide a more extensive set of complementary features that address a wide array of challenges across multiple cloud environments. These solutions are typically more versatile and can support a broader range of use cases. Critical mass features that establish a vendor as a platform player include multicloud and multiplatform support, automated disaster recovery, policy-based backup and retention, and comprehensive security measures such as user-managed encryption, two-way security ecosystem integration, and à la carte, solutions-based feature bundling.
The Sonar graphic reveals distinct clusters of vendors along the Feature Play/Platform Play axis.
Vendors are leveraging AI and ML to enhance threat detection, automate data classification, and optimize backup processes. This allows for proactive identification of potential threats and efficient data management.
Innovations in cyber resilience include features like data immutability, automated remediation, and ransomware detection. These capabilities ensure that data remains secure and recoverable even in the face of sophisticated cyber threats.
Cloud-native architectures enable vendors to offer scalable and flexible solutions that can adapt to varying workloads and data volumes. This includes the use of microservices, containerization, and orchestration tools like Kubernetes to ensure high availability and efficient resource utilization.
Vendors are developing unified management platforms that provide centralized visibility and control over data protection activities across multiple cloud environments. This simplifies operations and enhances compliance with regulatory requirements.
Innovations in cost management include consumption-based pricing models, global deduplication, and intelligent data compression. These features help organizations optimize their storage costs and ensure they pay only for what they use.
This emphasis on innovation highlights the dynamic nature of the cloud-native data protection market, in which rapid technological advancements and new feature introductions are crucial for staying competitive. The presence of numerous Forward Movers and disruptive Challengers suggests that the market is still evolving, with many vendors striving to outpace market demands through continuous innovation.
There is a noticeable concentration of Leaders on the Platform Play side. This distribution suggests that vendors offering a broad set of capabilities across multiple cloud environments are more likely to be recognized as Leaders because they can address a wider range of customer needs. Forward Movers are concentrated in the Feature Play segment, indicating that their core focus is on specific areas such as deeper, more thorough coverage and existing market-differentiating capability. Fast Movers are innovating on multiple fronts such as the breadth of SaaS targets or their user-driven low/no-code development capabilities to rapidly address the furious pace of change in applications and SaaS. Forward-moving platform players are concentrating on demonstrating delivery on roadmap items and paying down technical debt from complementary technology acquisitions to drive a unified product strategy. Fast Movers are demonstrating greater effort and focus on closing the gap between themselves and their leading competitors in their space.
A few vendors are shown to be moving from the Feature Play segment to the Platform Play segment, reflecting their strategic shifts and evolving capabilities. For instance, some vendors initially positioned as disruptive Challengers in the Feature Play segment are moving toward becoming competitive Leaders in the Platform Play segment. This movement indicates a trend by which vendors are expanding their feature sets and enhancing their platforms to provide more comprehensive solutions, thereby increasing their market competitiveness.
Comparing the current Sonar graphic with the previous year’s chart reveals several notable changes. Some vendors have progressed as anticipated, moving closer to the Leaders band due to their continuous innovation and expanded capabilities. For example, vendors like Clumio and Druva have shown significant improvement, aligning with the expectations they set in the previous year.
New vendors in this year’s evaluation, such as KeepIt and N-able, reflect the market’s ongoing evolution and the emergence of new players with promising capabilities. Conversely, some vendors from the previous year, such as Appranix (now a part of Commvault) and Google, are no longer prominently featured, possibly due to acquisition or a shift in market focus.
In reviewing solutions, it’s important to keep in mind that there are no universal “best” or “worst” offerings; there are aspects of every solution that might make it a better or worse fit for specific customer requirements. Prospective customers should consider their current and future needs when comparing solutions and vendor roadmaps.
5. Solution Insights
Acronis: Cyber Protect Cloud
Solution Overview
Acronis Cyber Protect Cloud is a comprehensive platform that integrates data protection, cybersecurity, and endpoint management into a single solution. Founded in 2003 and headquartered in Switzerland, Acronis focuses on providing robust cyber protection for data, applications, and systems. The platform is modular, offering both software and SaaS versions that support multiple modules called “Advanced Packs” for extended capabilities.
Acronis Cyber Protect Cloud’s centralized management components services are maintained by Acronis and hosted in Acronis Cloud data centers. All crucial management components are independently and dynamically scalable since they are all running in containerized Kubernetes-based environments. Management components consist of over 50 different microservices, each with separate management in terms of scaling and performance monitoring.
Given Acronis’s packaging of the solution as a SaaS, the Acronis Cyber Protect Cloud platform simplifies the user experience by concealing all the underlying complexity from end-users and partners. This approach eliminates the need for maintaining a local management server and managing its scalability, which is often the most challenging aspect of scaling on-premises solutions.
The solution supports a range of devices and platforms, ensuring fast RPO and RTO through technologies like universal restore and instant restore. Acronis’ unique approach lies in its integration of cybersecurity features with traditional data protection, offering functionalities like malware scanning of backups and AI-based threat detection.
Strengths
Acronis Cyber Protect Cloud excels in several areas. Its integration of data protection and cybersecurity into a single platform is a significant advantage, providing comprehensive protection vs. a range of threats. The solution supports a broad array of devices and platforms including legacy systems and mobile devices, which is a competitive edge over its rivals.
The firm also offers flexible deployment models, from cloud to hybrid to on-premises all leveraging the same cloud-native functionality. The platform’s modularity allows for easy scalability and customization, making it suitable for both small and large enterprises. It also has native integrations with over 200 other platforms and tools and the software is localized into 25 languages.
Additionally, company’ extensive global data center network ensures data residency and compliance with local regulations, enhancing its appeal to multinational organizations.
Challenges
One of the challenges of Acronis Cyber Protect Cloud is its configuration complexity. Given the solution’s breadth and depth, it may require significant time and resources for initial setup and configuration. The integration of multiple advanced features, while beneficial, can also lead to a steep learning curve for new users. Additionally, the reliance on a private network for SaaS delivery might pose flexibility limitations compared to fully public cloud solutions.
Purchase Considerations
Prospective buyers should consider the need for professional services and training to fully leverage Acronis Cyber Protect Cloud’s capabilities. For large-scale deployment, Acronis recommends the use of professional services to facilitate successful deployments. Investing in comprehensive training for IT staff can mitigate the solution’s complexity and ensure optimal use. Additionally, evaluating the vendor’s support services and understanding the costs associated with advanced features and modules will be crucial for budgeting and planning.
Acronis Cyber Protect Cloud serves a broad range of use cases including cloud-to-cloud backup for Microsoft 365 and Google Workspace, large-scale recovery after malware attacks, and real-time protection of important documents in edge locations. It is a general-purpose solution suitable for various industries, from SMBs to large enterprises. The platform’s flexibility and extensive feature set make it particularly appealing to MSPs and IT professionals seeking a unified solution for data protection and cybersecurity.
Sonar Chart Overview
Acronis Cyber Protect Cloud is positioned just inside the Leaders band, moving toward becoming a competitive Leader in this space. While Acronis is recognized for its leadership in the market, it is still in the early stages of establishing a dominant presence. The solution is a Forward Mover because it’s evolving at a pace that aligns with market demands. The focus on a balanced play indicates that Acronis is striving to offer a comprehensive solution that integrates both feature-specific and platform-wide capabilities. This balanced approach aims to address a broad range of customer needs, enhancing its competitive edge in the market.
AWS: AWS Backup
Solution Overview
AWS Backup is a fully managed service from Amazon designed to centralize and automate data protection across AWS services, both in the cloud and on-premises. AWS, a leader in cloud computing, focuses on providing scalable, secure, and cost-effective cloud solutions. AWS Backup is part of AWS’s extensive portfolio, integrating seamlessly with other AWS services like Amazon EBS, Amazon S3, Amazon EC2, Amazon RDS, Amazon Redshift, Amazon EFS, and Amazon FSx.
The solution allows users to create backup policies, known as backup plans, which define backup requirements and schedules. These plans can be applied to AWS resources using tags, ensuring consistent and compliant backups.
AWS Backup also supports features like immutability, encryption, centralized billing, cost allocation tags, restore testing, and logically air-gapped vaults, enhancing security and cost management. The service’s unique approach lies in its deep integration with the AWS ecosystem, providing a unified and automated backup management experience that is scalable and compliant with various regulatory standards.
Strengths
AWS Backup offers several strengths that make it an attractive option for organizations aiming to centralize and automate their data protection strategies. A key advantage is its centralized management capability, providing a single console, APIs, and the AWS command-line interface (CLI) to manage backups across various AWS services. This simplifies operations, enabling users to create and manage consistent backup policies across all AWS resources, ensuring comprehensive and compliant data protection.
Scalability is another significant strength. AWS Backup can seamlessly scale with organizational growth, accommodating increasing data volumes without requiring major infrastructure changes. This is crucial for businesses experiencing rapid growth or fluctuating storage needs.
Security and compliance are also notable strengths. AWS Backup uses advanced encryption to protect data in transit and at rest and adheres to numerous compliance certifications, including SOC, ISO 27001, and HIPAA. This helps organizations meet regulatory requirements and maintain robust data protection strategies.
The pay-as-you-go pricing model of AWS Backup reduces TCO by eliminating the need for physical backup infrastructure. Organizations pay only for the storage and data transfer they use, making it a cost-effective solution for businesses of all sizes.
Lastly, AWS Backup excels in automation, reducing the need for manual intervention and custom scripts. Automated tasks ensure consistent and reliable backups, while lifecycle management policies optimize storage costs by transitioning backups to lower-cost storage tiers based on predefined schedules.
Challenges
AWS Backup, despite its many strengths, presents several challenges. Managing cross-region backups is one of the primary difficulties. Although AWS Backup supports this feature, it often requires creating multiple backup vaults, which can increase management complexity and overhead, particularly for organizations with extensive, geographically dispersed data.
Another significant challenge is the limited granular restoration options. For services like Amazon Elastic File System (EFS), AWS Backup’s granular file-level restore for Amazon EFS faces challenges like case-sensitive paths, no wildcard support, a 10-item console limit, restore directory clutter, and performance constraints. Multiple restores create numerous directories, complicating file management and potentially impacting restore times and accuracy.
Additionally, AWS Backup’s scripting and configuration complexity can be daunting. While the service offers robust automation capabilities, advanced backup operations often require scripting and manual configuration, demanding a good understanding of AWS SDKs, APIs, and scripting languages like Python or shell scripts. Organizations lacking this expertise might struggle to fully leverage AWS Backup, resulting in suboptimal backup strategies and increased operational overhead.
Moreover, AWS Backup’s restore capabilities have certain limitations. For instance, it does not offer advanced options like point-in-time recovery for all database types other than RDS, Aurora, and SAP HANA on EC2, or the ability to restore systems in a specific order to meet application dependencies. Complex recovery scenarios or disaster recovery drills may require additional AWS services like AWS Lambda and Restore Testing to create custom scripts or workflows, further complicating the backup and recovery solution.
Purchase Considerations
When considering AWS Backup, it is essential to evaluate the need for professional services and training. Organizations may require support for initial setup and ongoing management, especially for complex backup configurations. AWS offers extensive documentation and support, but leveraging AWS partners or 3rd-party solutions can provide additional expertise and streamlined management. Regular audits and performance monitoring are recommended to ensure backup integrity and compliance.
AWS Backup serves a range of AWS-specific use cases and market segments, making it a general-purpose solution. It is for enterprises of all sizes, from startups to large-scale organizations, across various industries. Key use cases include disaster recovery, regulatory compliance, and data protection for AWS-native VMs, databases, or file systems, and ransomware recovery. Cloud-mature industries such as finance, healthcare, and technology, which require stringent data protection and compliance, can particularly benefit from AWS Backup’s robust features and scalability.
Sonar Chart Overview
AWS Backup is positioned on the outer edge of the Challenger circle, indicating it has established itself in the market but is not yet a dominant player. The solution is moving toward becoming a disruptive Challenger: it is improving rapidly and gaining traction. As a Forward Mover, it is evolving at a pace that matches market demands, aiming to enhance its innovation capabilities. This trajectory toward a more innovation-focused solution highlights AWS Backup’s commitment to introducing significant new features and improvements, which are likely to disrupt the market and challenge existing leaders. This positioning reflects AWS Backup’s potential to become a key player in cloud-native data protection.
Backblaze: Cloud Backup
Solution Overview
Backblaze is a cloud storage and backup company founded in 2007. The company focuses on providing affordable, easy-to-use cloud storage solutions for both individuals and businesses.
It offers 2 primary products: B2 Cloud Storage and Computer Backup. The Computer Backup solution is a standalone product designed to automatically back up all files on a user’s computer, including external drives, with unlimited storage for a flat fee. It is part of a larger portfolio that includes B2 Cloud Storage, which is aimed at developers and businesses needing scalable object storage. The Computer Backup solution works by continuously backing up files in the background, ensuring data is always up-to-date and secure. It offers mass deployment and user/group management support to help enable organization admins to easily provision, manage and control billing with enterprise-grade controls. It supports both Mac and PC and offers features like private encryption keys, two-factor authentication, and the ability to restore data via web, mobile apps, or shipped hard drives.
Backblaze’s approach is straightforward and user-friendly, making it accessible to non-technical users, which sets it apart from more complex solutions offered by competitors.
Strengths
Computer Backup solution stands out for its cost-effectiveness, simplicity, security, and scalability, making it an attractive option for individuals and businesses alike.
One of its key strengths is the competitive pricing: unlimited backup for a flat $99 yearly or $9 monthly fee per computer. This model is particularly advantageous for users with large data volumes, as it avoids escalating costs with increased storage needs.
The service is designed for ease of use, with a straightforward setup that requires minimal configuration. Once installed, it runs automatically in the background, continuously backing up user files without user intervention. This “set and forget” approach ensures data protection without constant monitoring.
Security is another strong point for Backblaze. It offers private encryption keys, two-factor authentication, and data encryption both in transit and at rest. For businesses, the enterprise control feature adds fine-grained access permissions, advanced SSO with OIDC support, expanded group management, and agent removal prevention, ensuring robust data protection.
Backblaze also provides multiple data restoration options, including web downloads, mobile apps, and physical hard drive shipments, ensuring quick and efficient data recovery.
Designed to scale, Backblaze is suitable for both individual users and businesses, efficiently meeting diverse Windows and Mac backup needs. This scalability is particularly beneficial for a range of customers from small to medium-sized businesses anticipating growth to enterprises with over 10,000 users and MSPs servicing large user communities.
Challenges
A significant drawback is the lack of advanced customization options. Designed for simplicity, Computer Backup offers a number of granular controls over backup settings, including backup scheduling and throttling, and ability to exclude items a user or organization does not wish to back up. To be sure, the product does not always serve edge case control needs, such as the ability to schedule backups for different times on different days of the week. Backblaze may not provide the granular control over backup settings that advanced users or IT professionals might need. This can be a limitation for those requiring specific backup configurations tailored to unique needs.
Additionally, Backblaze’s de-dupe capabilities are limited, operating mainly at the local client level on individual computers rather than across multiple devices or accounts. This could lead to increased bandwidth consumption due to the need to upload the same file that may be present across multiple endpoints multiple times. Additionally, because Computer Backup service supports unlimited backup for a flat fee, de-dupe actually has no bearing on storage cost.
Another limitation is the absence of advanced cyber protection features such as data malware detection and limited immutability capabilities. Although Backblaze’s B2 Cloud Storage offers immutable storage capabilities, this feature is mimicked in the form of a “forever” retention policy available in the backup product.
Moreover, Backblaze does not support full disk image backups, meaning it cannot create a complete snapshot of a system, including the OS, applications, and settings. This can be a significant drawback for users needing a comprehensive backup solution for full system recovery in the event of a catastrophic failure.
Understanding these limitations can help potential users make an informed decision about whether Computer Backup solution meets their specific needs.
Purchase Considerations
Potential buyers should consider their specific needs for data protection and recovery. While Backblaze offers excellent value and ease of use, users needing full disk image backups or more advanced customization may require additional solutions. Evaluating the need for professional services or training is a minor task due to the product’s simplicity, but businesses might benefit from premium support options made available through its enterprise control offering for faster response times and dedicated technical account management.
Backblaze’s solution is broadly focused, serving a wide range of market segments including individual users, SMBs, and educational institutions. It is particularly well-suited for industries that require straightforward, cost-effective endpoint data protection without the need for complex configurations, such as education, healthcare, and creative services. The solution’s affordability and ease of use make it an attractive option for users looking for reliable, set-and-forget backup capabilities.
Sonar Chart Overview
The vendor is positioned on the outer edge of the Challenger circle, as it is still maturing but shows significant potential. The solution is a Forward Mover, as it is evolving at market pace and adapting to market demands. Its focus on maturity over innovation means it is less likely to introduce substantial new features and improvements, aiming to invest further into improving its core capabilities. This positioning reflects firm’s commitment to providing cost-effective, scalable, and secure cloud backup solutions, as evidenced by its competitive pricing, robust security features, and continuous product enhancements.
Clumio
Solution Overview
It is a cloud-native data protection company that focuses on simplifying and securing data backups for modern cloud environments. The primary offering is a single, integrated platform designed to provide comprehensive backup and recovery services for various AWS workloads including S3, EC2, EBS, RDS, Aurora, DynamoDB, Microsoft SQL ServerL on EC2, and Microsoft 365.
Firm’s solution is characterized by its serverless architecture, leveraging AWS Lambda functions for operations, which ensures scalability, flexibility, and resilience. The platform is entirely SaaS-based, requiring no deployment or configuration tasks from the customer, and it operates autonomously with bi-weekly updates. Company’s unique approach includes air-gapped, immutable backups, and a consumption-based pricing model, setting it apart from traditional, server-based backup solutions.
Strengths
Firm’s cloud-native data protection solution stands out for its scalability, security, and cost-efficiency. Its serverless architecture supports petabyte-scale environments and millions of changes per hour, making it for large enterprises. The platform ensures robust security with air-gapped, immutable backups and multilevel encryption, protecting vs. ransomware and other threats.
As an agentless and SaaS-based solution, the product requires minimal setup and maintenance, reducing operational overhead. Users can deploy the platform in under 10 minutes, streamlining compliance and security management. Firm’s consumption-based pricing, combined with intelligent data compression and no in-account data processing costs, offers significant savings over traditional backup solutions. Its FinOps capabilities provide insights into cloud spending, optimizing resource usage and cost-saving measures.
The company also excels in recovery times with features like “instant access” and massively parallel restores, allowing near-instantaneous recovery without rehydrating data into AWS accounts. This approach minimizes downtime for critical applications. Overall, Clumio provides a scalable, secure, and cost-effective data protection solution, simplifying operations and ensuring rapid recovery for modern cloud environments.
Challenges
Vendor’s support for non-AWS cloud platforms is limited. While it excels in AWS environments, its support for platforms like Microsoft Azure is still developing. This can be a drawback for enterprises needing a unified data protection solution across multiple clouds. The company is working to expand its multicloud capabilities, but currently, it lags behind some competitors.
Firm’s application-aware instant recovery capabilities are not as comprehensive as AWS Backup, which offers broader component services for application-level recovery. Clumio is enhancing its workload coverage and reliability, but these improvements are still in progress.
Additionally, it does not perform data movement optimizations such as source-side de-dupe and compression. This design choice prioritizes security and simplicity but may lead to higher data transfer and storage costs compared to solutions with advanced data reduction techniques.
The firm lacks support for traditional workloads like endpoint, NAS, and hypervisor targets. This limitation can be significant for organizations with a mix of legacy and cloud-native workloads, potentially requiring multiple backup solutions and increasing complexity.
While firm’s serverless architecture offers excellent scalability within AWS, its performance in non-AWS environments remains uncertain as it expands to other cloud platforms.
Purchase Considerations
While the company offers a straightforward setup, enterprises with complex environments may benefit from professional services to optimize their backup strategies and ensure seamless integration. The vendor provides technical account managers for an additional fee, which can be valuable for ongoing support and ensuring successful backup and recovery operations. Investing in training for IT staff on Clumio’s platform can enhance the effectiveness of the solution and ensure best practices are followed.
Clumio’s solution is versatile, addressing a broad range of use cases including ransomware recovery, operational backup and recovery, data compliance, disaster recovery, and storage cost optimization. It is for industries with stringent data protection requirements such as financial services, healthcare, and media. The platform’s scalability and performance make it for large enterprises and digital-native companies with extensive AWS cloud footprints looking for a more specialized solution than what is natively offered by the cloud provider.
Sonar Chart Overview
Clumio’s solution is positioned as a disruptive Challenger, and it shows significant potential to move into the Leaders band in the near future. This forward movement is driven by its innovative cloud-native data protection capabilities, which leverage serverless architecture and efficient scaling. Vendor’s orientation as a Feature Play, rather than a Platform Play, indicates its strength in providing specialized, high-performance data protection features such as air-gapped backups and rapid recovery, tailored to specific needs. This positioning reflects firm’s ability to outpace market demands and innovate rapidly, making it a strong contender in this space.
Commvault: Cloud Platform
Solution Overview
Commvault Systems offers the Cloud Platform, a comprehensive cyber-resilience solution designed to meet the needs of hybrid enterprises. This platform integrates data protection, cyber recovery, Cloud Native App re-build and operational efficiency into a unified suite, supporting a wide range of workloads, including legacy applications, databases, VMs, containers, and SaaS applications. This ensures seamless data management across on-premises, hybrid, and multicloud environments.
The platform is powered by Metallic AI, which leverages AI, ML, natural language processing (NLP), and automation to enhance threat detection, cyber recovery, and operational efficiencies. It is not a standalone product but part of a larger suite that includes integrated components such as data risk governance, early warning systems, and AI-supported automation. This holistic approach differentiates Commvault from its peers by offering a unified, extensible platform that addresses diverse data protection needs.
Commvault Cloud intends to provide the necessary components to recover data, applications, and infrastructure at the lowest total cost. True cyber resilience requires security and IT teams to work together across an infinitely variable number of workloads, applications, and infrastructure, which can be complex. Cloud Platform delivers the broadest and deepest set of capabilities to address data threats, attack tactics, continuous validation, forensic analysis, and recovery needs across legacy on-prem, shared storage, endpoint, VM, public, private, and SaaS clouds all in a unified and extensible platform.
Beyond cyber resilience, the company improves other critical business initiatives, including data risk governance, early warning capabilities, readiness and response, cyber recovery, cloud native application resource, dependency mapping, and full re-building. The platform’s AI-driven capabilities, such as threat prediction and active defense, provide proactive security measures.
Strengths
Commvault Cloud stands out for its extensive workload coverage and enterprise-level resilience. It supports all major hyperscalers (AWS, Azure, GCP, and Oracle Cloud Infrastructure) and integrates seamlessly with various identity and access management solutions, SaaS applications, and traditional workloads. Its “any-to-any” portability feature allows flexible data recovery across different environments, enhancing disaster recovery and cyber resilience.
The platform’s AI-driven capabilities, such as threat prediction and active defense, offer proactive security measures. Commvault’s acquisition of Appranix further extends its cyber recovery and resilience capabilities in the hyperscaler space to discover and rebuild cloud native apps, making it a robust solution for modern enterprises. Its support for a range of workloads and environments, combined with advanced AI and ML capabilities, positions it as a leader in data protection and cyber resilience.
A notable feature of Cloud Platform is its Cleanroom Recovery technology and Air Gap Protect, which pairs immutable SaaS storage with access to a Commvault-managed Azure tenant for BC. This technology creates a secure, isolated environment for cyber recovery testing, forensic analysis, and data recovery, automating the recovery process and ensuring quick, secure recovery from cyber incidents without reinfection. The ability to automate and prioritize recovery workflows, including restoring accounts, permissions, and credentials, enhances the platform’s resilience and operational efficiency.
Firms AI-supported automation layer combines AI, ML, NLP, heuristics, and automation to quickly identify threats, accelerate cyber recovery, drive operational efficiencies, and improve the TCO of protecting hybrid cloud workloads. Its generative AI interactions, through the AI co-pilot Arlie, provide personalized, actionable responses, enhancing the user experience. These comprehensive capabilities make Commvault ideal for enterprises with complex, hybrid IT environments seeking robust data protection and cyber resilience solutions.
Challenges
One significant challenge is the complexity of the platform, which can result in a steep learning curve for new users. This complexity necessitates substantial onboarding and training efforts to leverage the platform’s capabilities fully. Additionally, while Cloud Platform offers robust security features, there is room for improvement in performance and hardware requirements, particularly for software and SaaS-based deployments.
For customers looking for SaaS, another notable challenge is that the management plane of the Cloud Platform is hosted exclusively on a single hyperscaler, Microsoft Azure. Although there is geographical redundancy to prevent regional outages, the reliance on a single cloud provider could be viewed as a limiting factor for the resiliency of the management plane of the overall Commvault solution in the event of a provider-wide outage. Addressing these challenges would enable the vendor to enhance its appeal to a broader range of customers and ensure seamless integration across diverse IT environments.
Purchase Considerations
Prospective buyers should consider the need for professional services and training to leverage Cloud Platform’s capabilities fully. The platform’s complexity may necessitate ongoing support and consultation to optimize its use. It is also advisable to assess the vendor’s support and training offerings to ensure that the organization can effectively manage and use the platform.
Additionally, organizations should evaluate their existing infrastructure and readiness for integration with Commvault’s advanced features, ensuring compatibility and seamless deployment.
Optional add-ons like Air Gap Protect, HyperScale X, Risk Analysis, Cleanroom Recovery, and Appranix Rebuild are available with all solution packages. These add-ons can enhance the platform’s capabilities but also increase the overall cost. The vendor offers several bundled packages, such as Operational Recovery, Autonomous Recovery, Cyber Recovery, and Platinum Resilience. Each bundle includes different sets of features, and customers should carefully evaluate which bundle meets their needs to avoid paying for unnecessary features.
The company serves a range of use cases, including ransomware and cyber defense, data compliance, backup and recovery, and cloud migration. It is designed for general-purpose use across various industries, from finance and healthcare to manufacturing and government.
The platform’s comprehensive capabilities make it for enterprises with complex, hybrid IT environments seeking robust data protection and cyber resilience solutions. Its ability to support a range of workloads and environments makes it a versatile solution for organizations of all sizes and industries. Commvault Cloud’s extensive workload coverage and enterprise-level resilience make it a solution for organizations looking to enhance their cyber resilience and data protection strategies.
Sonar Chart Overview
Cloud Platform, powered by Metallic AI, is positioned as a competitive Leader in this space. This positioning reflects its robust capabilities in cyber resilience, data protection, and recovery, which are critical in the hybrid cloud enterprise landscape. The platform’s forward movement indicates its rapid innovation and adoption of advanced AI-driven features, such as Threat Scan Predict and Cleanroom Recovery, which enhance its resilience and recovery capabilities. The focus on a balanced play suggests that the vendor is effectively integrating both feature-specific and platform-wide solutions, aiming to provide comprehensive, scalable, and efficient data protection across diverse environments.
Druva: Data Security Cloud
Solution Overview
Druva is a provider of cloud-native data protection solutions, focusing on data resiliency and security. The company’s primary offering, Data Resiliency Cloud, is a comprehensive, fully managed SaaS platform designed to protect and manage data across various environments, including endpoints, data centers, AWS, Azure, and SaaS applications.
The solution integrates a range of features such as backup and recovery, DR, archiving, cyber resilience, legal hold, and compliance monitoring into a single platform. Firm’s unique approach includes features like accelerated ransomware recovery, air-gapped backups, and global de-due, which are not commonly found in peer solutions. The platform is designed to be intuitive and easy to manage, providing a unified console for comprehensive data protection and security management.
Strengths
Data Resiliency Cloud offers native data protection for AWS workloads including EC2, EBS, and various AWS databases like RDS, Aurora, DynamoDB, Redshift, DocumentDB, and Neptune. It also supports cloud-hosted databases across multiple public clouds, ensuring data safety regardless of location.
A key feature is its advanced DR and cyber resiliency capabilities. The firm provides accelerated ransomware recovery with quarantine and orchestrated recovery based on curated snapshots, ensuring files are restored to their last known good state. The cloud DR feature offers one-click, policy-driven failover and failback with testing capabilities available in all AWS regions, achieving an RPO of up to an hour and an RTO in minutes.
The company also excels in legal hold, e-discovery, and compliance, supporting GDPR and CCPA. It streamlines legal processes by collecting and preserving data during backups, offering pre-culling, audit trails, and API integrations with 3rd-party solutions like Exterro. Teams can conduct global metadata searches across workloads including Microsoft 365, Salesforce, Google Workspace, and endpoint devices.
The intuitive management console provides centralized visibility, control, and monitoring, with metrics, federated search, and storage insights. As a fully managed SaaS platform, the vendor eliminates hardware and maintenance costs, offering consumption-based pricing and globally deduplicated storage to reduce costs.
It supports on-premises and SaaS workloads, including recent additions for Microsoft Azure, enabling secure, air-gapped backups with no egress fees and global de-dupe. This versatility ensures seamless data protection across various environments. Overall, Data Resiliency Cloud is notable for its comprehensive protection, advanced recovery features, robust compliance support, ease of use, cost efficiency, and versatility.
Challenges
A primary concern is its heavy reliance on AWS as its infrastructure backend. While this offers seamless support for AWS workloads, it poses a risk for organizations preferring a multicloud strategy, potentially limiting flexibility and resilience if AWS services or pricing change.
Additionally, the vendor supports VMs, files, and databases across AWS and Azure but lacks native VM support for GCP. This gap can be significant for organizations with GCP infrastructure, necessitating additional data protection solutions and complicating data management strategies.
Another issue is the absence of cloud seeding capabilities, which are crucial for efficiently migrating large volumes of data from on-premises to the cloud. Without this feature, the initial data transfer can be time-consuming and bandwidth-intensive, delaying deployment and increasing costs.
Furthermore, firm’s instant restore capabilities are limited to VMware workloads, despite its support for other non-VMware VMs. This restriction can be problematic for organizations with diverse virtual environments.
These challenges highlight areas where company’s solution may need to evolve. Organizations should evaluate these factors against their specific requirements to ensure Data Resiliency Cloud aligns with their data protection strategy.
Purchase Considerations
Organizations considering the vendor should ensure they have a clear understanding of their data protection needs and the specific environments they operate in. It is advisable to engage with company’s professional services for initial setup and configuration to maximize the solution’s potential. Additionally, training for IT staff on the platform’s features and capabilities can help in leveraging its full benefits. Evaluating the support options and SLAs provided by the firm will also be crucial for ensuring ongoing operational efficiency and quick issue resolution.
Firm’s solution is versatile, addressing a range of use cases across various market segments. It is particularly suited for industries with stringent data protection and compliance requirements such as healthcare, finance, and legal sectors. The platform’s ability to protect data across endpoints, cloud environments, and SaaS applications makes it a general-purpose solution, catering to both small and large enterprises looking to modernize their data protection strategies across a data estate and enhance cyber resilience all under a single umbrella solution.
Sonar Chart Overview
Data Security Cloud is positioned as a solid Leader, reflecting its current status as a robust solution with significant potential for growth and improvement. The solution is a Fast Mover, indicating it is rapidly evolving and adapting to market demands. Its trajectory toward improvement along a balanced play axis suggests that the vendor is enhancing both its innovation and maturity, as well as its feature and platform capabilities. This balanced approach ensures that the firm introduces new, innovative features and also maintains a stable and comprehensive platform, making it a strong contender in the cloud-native data protection market.
HYCU: R-Cloud Platform
Solution Overview
HYCU is a data protection company specializing in cloud-native data protection, data migration, and DR. The company’s primary offering, R-Cloud, is a SaaS platform designed to provide comprehensive data protection across on-premises, cloud services, and SaaS applications. The platform includes HYCU R-Graph for data estate discovery and visualization, supporting nearly 70 data sources.
R-Cloud is a single, integrated platform offering automated backup, granular restore options, and DR capabilities. It is delivered as a true cloud-native SaaS solution with an agentless architecture, eliminating the need for additional hardware or software. Company’s unique approach leverages AI-powered, low-code development to rapidly extend protection to new data sources, setting it apart from traditional data protection providers.
R-Cloud’s architecture is built to be easily extensible to new data sources to scale protection to cover new data sources quickly and easily through AI-powered low-code development. The firm has partnered with Anthropic to build an AI that uses knowledge of the R-Cloud architecture to decrease the build time for new data protection modules to hours, as opposed to the months or years it takes legacy data protection providers to build capabilities to cover new data sources.
In addition to rapid development capabilities, the vendor was also built to support 3rd-party developers, which provides firm’s partners, SaaS vendors, and independent developers with the opportunity to partner with the company to build and monetize data protection modules.
Strengths
The platform supports cloud-native ephemeral service delivery across multiple major and minor public cloud providers, including AWS, Azure, and GCP, ensuring seamless integration and scalability. R-Cloud offers extensive encryption capabilities, using end-to-end AES-256 encryption for data at rest and in transit, and supports user-managed keys and key rotation, enhancing data security and compliance.
The solution provides fine-grained recoverability, allowing users to restore data down to the file, object, or element level. It also features cloud-aware dependency mapping and resource recoverability, ensuring that both data and configurations can be restored accurately and efficiently. R-Cloud employs global application-aware de-dupe and compression, optimizing storage usage and reducing costs without compromising performance.
R-Cloud supports an extensive list of SaaS data sources, providing comprehensive data protection across a range of applications. At a high level, the solution supports the Atlassian product suite, collaboration and productivity tools, development and DevOps tools, customer identity and access management, CRM and marketing, and other niche apps. R-Cloud’s extensive support for these SaaS data sources ensures that organizations can protect a wide array of critical applications and services, providing robust data protection and recovery capabilities tailored to each specific data source.
Additionally, R-Cloud includes HYCU R-Graph, a built-in discovery and visualization tool that helps organizations map their data estate, identify unprotected data, and ensure compliance with data protection standards. This comprehensive visualization capability enables technology leaders to quickly identify gaps in data protection and verify adherence to data retention and storage policies.
Challenges
One of the primary challenges for R-Cloud is brand recognition. Despite having over 4,000 global customers, the company is a relatively young company and is not as well-known as some of its more established competitors.
Given its history as an on-premises virtualization backup provider, it seems uncharacteristic of the solution not to offer a cloud seeding capability. Additionally, while the platform offers extensive data protection capabilities, it may not cover all legacy systems or niche applications, which could be a limitation for some potential customers.
Purchase Considerations
Prospective customers should consider the need for professional services and training to fully leverage R-Cloud’s capabilities. Evaluating compatibility with existing IT infrastructure and specific data protection requirements is crucial for seamless integration and maximum benefit.
R-Cloud serves a range of use cases, including data estate discovery and visualization, automated and on-demand backups, ransomware protection and recovery, DRaaS, compliance and eDiscovery, and data migration and mobility. It is designed for various market segments, including cloud service providers, MSPs, large enterprises, multinational corporations, and government and public sector organizations, making it suitable for an array of industry verticals.
Sonar Chart Overview
The R-Cloud Platform is positioned as a solid Leader, reflecting its nascent but promising capabilities in the cloud-native data protection market. The platform’s fast movement toward improvement along a balanced play indicates its dual focus on both innovation and maturity, as well as feature and platform plays. R-Cloud’s rapid development and integration of comprehensive data protection features for a range of SaaS applications, combined with its low-code development environment, demonstrate its potential to disrupt the market and enhance its competitive stance.
KeepIt
Solution Overview
KeepIt is a company dedicated to providing cloud-native data protection solutions, primarily focusing on SaaS applications. Founded in 2013, it has built a reputation for offering secure, reliable, and cost-effective data backup and recovery services. The company’s flagship product, KeepIt Cloud, is a comprehensive, vendor-neutral solution designed to protect data across various SaaS platforms, including Microsoft 365, Google Workspace, Salesforce, and Microsoft Dynamics 365.
KeepIt Cloud is a standalone product that operates independently of public cloud infrastructures, running on firm’s own data centers and hardware. This approach ensures that backup data is stored in a logical infrastructure that’s separate from the primary data, enhancing security and resilience. The solution leverages advanced technologies such as a blockchain-like Merkle tree architecture and “incremental forever” data transfer to provide efficient, long-term storage and fast recovery options.
Strengths
Company’s vendor-neutral approach ensures compatibility with a range of SaaS applications, reducing the complexity and risk associated with managing multiple backup systems.
The solution’s architecture, which includes dual data center redundancy and immediate encryption of backup data, provides robust security and resilience against data loss and cyber threats. Additionally, firm’s use of a proprietary storage infrastructure allows for predictable, all-inclusive pricing without hidden fees for storage consumption or API transactions.
The platform’s ease of use, with features like Smart Search and a modern web-based interface, ensures that DR is quick and straightforward. Furthermore, company’s compliance with international security standards such as ISO 27001 and ISAE 3402 underscores its commitment to maintaining high levels of data protection.
Challenges
One notable area for improvement is the lack of automated testing within the SaaS backup solution, which requires customers to manually verify the integrity of their backups.
Additionally, while the solution is comprehensive for its supported list of targets, it may not cover all potential market-dominant SaaS applications out-of-the-box, necessitating ongoing updates and integrations to keep pace with new SaaS offerings.
Purchase Considerations
Prospective customers should consider the need for professional services and training to fully leverage firm’s solution. While the platform is designed to be user-friendly, initial setup and configuration, especially in complex environments, may benefit from expert assistance.
Additionally, organizations should ensure they have robust internal processes for regular backup verification and testing, given the lack of automated testing features. Firm’s support for multifactor authentication and role-based access control (RBAC) should also be used to enhance security.
Vendor’s solution is broadly applicable across various industries, making it suitable for both SMBs and large enterprises. It is particularly valuable for organizations heavily reliant on SaaS applications, such as those in the technology, education, and professional services sectors. The solution’s comprehensive coverage of major SaaS platforms and its robust security features make it a choice for businesses seeking to ensure data protection and compliance with international regulatory requirements like GDPR.
Sonar Chart Overview
The KeepIt solution is positioned on the outer edge of the Challenger circle, moving toward becoming a disruptive Challenger. This positioning reflects its growing capabilities and potential to significantly impact the cloud-native data protection market. KeepIt’s forward movement toward improvement along the innovation play axis indicates its focus on introducing new and advanced features. The solution’s emphasis on comprehensive SaaS data protection, compliance with stringent regulations like GDPR and NIS2, and robust ransomware resilience showcases its innovative approach. Vendor’s independent cloud infrastructure and granular recovery options further solidify its potential to disrupt the market and enhance its competitive stance.
Microsoft: Microsoft Azure Backup
Solution Overview
Microsoft’s Azure Backup service is an integrated data protection solution within the Azure public cloud platform. It uses Azure components to create application-consistent snapshots and offers various storage options – locally redundant, geo-redundant, or zone-redundant – based on data criticality and recovery needs.
Management is centralized through the Azure Business Continuity center, which provides insights into data protection plans and health overviews and allows for scalable enforcement of backup policies via Azure Policy. The service also includes auditing, analysis capabilities, and integration with 3rd-party monitoring systems.
Azure Backup enhances cyber resiliency with features like multiple-user authentication and additional authorization layers for critical operations. It includes a 14-day soft delete option to recover accidentally deleted backups and stores data separately from production workloads for added security. The immutable vault setting ensures backup data protection vs. malicious deletion attempts.
Integration with Microsoft Defender for Cloud (MDC) offers robust ransomware detection, enabling automated actions such as preserving recovery points and alerting backup admins. Customers can also configure cross-region data protection and use immutable snapshots for enhanced recoverability. Azure Recovery Services vaults support long-term data retention, including soft-delete and cross-region restores.
Azure Backup supports a range of services including Azure VMs, Managed Disks, SQL Server, SAP HANA, PostgreSQL servers, Azure Files, Blob Storage, and, recently, Azure Kubernetes Service (AKS) via the Velero project. However, some Azure database offerings are not yet covered, though the service can protect several on-premises workloads.
Strengths
Azure Backup offers robust encryption capabilities, ensuring data security both at rest and in transit. Data at rest is protected using 256-bit AES encryption, while data in transit is secured via HTTPS/TLS 1.2+ protocols. For on-premises backups, the Azure Recovery Services agent encrypts data with a passphrase before transmission, adding an extra layer of security.
Azure Backup supports customer-managed keys (CMKs) stored in Azure Key Vault, allowing users to employ a BYOK approach and manage key rotation. This feature provides full control over encryption keys, enabling key changes as needed. Additionally, Azure Backup integrates with Azure role-based access control (RBAC) for fine-grained access management and offers features like soft delete and immutability to protect against accidental or malicious deletions. These comprehensive security measures make Azure Backup a reliable solution for safeguarding critical data.
Challenges
Azure Backup is primarily an Azure Native backup solution for its cloud based workloads. It is a powerful solution for data protection, but it does have some challenges, particularly in the areas of data movement optimization and storage capacity efficiency.
It does not natively support bandwidth throttling for data movement from private to public cloud, which can lead to network congestion during backup operations. Users must rely on external methods, such as configuring network devices or using 3rd-party tools, to manage bandwidth usage.
The solution lacks built-in support for network path acceleration or caching capabilities, which are essential for optimizing data transfer performance and ensuring secure, low-latency connections between workloads, public or private workload environments, and the Azure Backup service.
Azure Backup does not offer a straightforward cloud seeding option for initial large-scale data transfers. While offline seeding is possible using Azure Data Box, it is not as seamless or integrated into the Azure Backup service as other solutions.
It noticeably does not provide built-in storage capacity efficiency capabilities. It does not provide de-dupe capabilities, which means that redundant data is stored multiple times, leading to inefficient use of storage space. The solution also lacks native compression features, which could otherwise reduce the amount of data transferred and stored, thereby optimizing storage costs and improving transfer speeds.
These limitations can impact the overall efficiency and cost-effectiveness of using Azure Backup, especially for organizations with large volumes of data or complex data protection requirements.
Purchase Considerations
Azure Backup pricing is based on the number of protected instances and the amount of storage used. Understanding the cost implications of different storage options – such as locally redundant storage (LRS) and geo-redundant storage (GRS) – and retention policies is crucial. The service has a fixed cost for protected instances and variable costs based on storage and bandwidth usage. It’s important to estimate these costs accurately using tools like the Azure Backup pricing estimator.
Azure Backup addresses a range of use cases and market segments, making it a general-purpose solution. It is suitable for small businesses needing cost-effective data protection, large enterprises requiring robust DR, and organizations with compliance and regulatory requirements. It supports various workloads, including on-premises and cloud-based VMs, SQL Server, SAP HANA, file shares, and Kubernetes clusters. It does not focus on a specific industry vertical but provides versatile data protection across multiple sectors.
Sonar Chart Overview
Azure Backup is initially scored as a competitive Challenger, moving toward becoming a disruptive Challenger. This positioning reflects its solid but evolving capabilities in cloud-native data protection. The solution’s forward movement toward improvement along the innovation play axis indicates a strong focus on introducing new, impactful features and technologies. Azure Backup’s comprehensive support for various workloads, including Azure VMs, SQL, SAP, and Kubernetes, combined with its robust security measures against ransomware, demonstrates its potential to significantly disrupt the market. The platform’s continuous enhancements, such as agentless multidisk crash-consistent backups and vaulted backups for Azure Files, underscore its innovative trajectory.
N-able: Cove Data Protection
Solution Overview
N-able provides IT service management solutions to empower MSPs and IT teams to tackle complex IT challenges efficiently. Cove Data Protection is a cloud-native SaaS solution tailored for the backup and disaster recovery of servers, workstations, and Microsoft 365 data.
Cove includes a web-based, multitenant management console and primary backup storage across more than20 global data centers. Its backend is supported by multiple Cove cloud environments, enabling direct-to-cloud backups without local appliances. Built on cloud-native principles, Cove emphasizes operational efficiency, reduced administrative overhead, and dynamic scalability. Unlike traditional snapshot or image-based products, Cove’s TrueDelta technology backs up only changed data fragments, ensuring efficient data transfer and storage.
Cove supports a range of data sources, including individual files, directories, and complex systems like SQL Server, VMware, Hyper-V, Exchange, SharePoint, Oracle, and MySQL. It also backs up OS configurations (system state data) and provides comprehensive protection for Microsoft 365 data, including Exchange, OneDrive, SharePoint, and Teams.
The solution supports both agent-based and agentless backups, offering deployment flexibility. Cove features file-level, application-level, and full system recovery, ensuring granular and comprehensive data protection. It excels in backing up server and endpoint devices (Windows, Linux, and Mac) using agent-based technology, with NAS backups supported through a Windows-based mount point.
Cloud-hosted VM servers rely on the Cove agent for protection, and its SaaS support primarily targets the Microsoft 365 ecosystem. Cove’s extensive support for Microsoft and Windows-based data sources makes it suitable for various use cases, from simple file backups to complex enterprise-level data protection needs.
Strengths
The TrueDelta architecture leverages byte-level file change tracking, which significantly reduces the amount of data that needs to be transferred during backups. This is achieved through advanced de-dupe and compression techniques, shrinking backups by up to 60x smaller than traditional methods. This efficiency allows for more frequent backups, improving RPOs.
Cove supports cloud seeding, which allows for the initial bulk upload of backup data to be performed via a removable storage device or network share. This data is then transferred to the cloud from a different machine with a high-speed internet connection. This process ensures that large initial backups do not overwhelm network bandwidth, facilitating a smoother transition to cloud-based backups.
Due to its architecture, all of Cove’s backup copies are isolated and immutable by default, with no need to make policy decisions around levels of protection. Local copies are secondary and optional.
Cove includes advanced DR features such as automated recovery testing and standby image technology. Recovery testing uses AI/ML-based boot detection to ensure that backup images are bootable, enhancing confidence in recovery processes. Standby image technology creates a bootable VM after each backup, which can be stored in environments like Hyper-V, VMware ESXi, or Azure. This ensures rapid recovery and business continuity in the event of a disaster.
Challenges
While the solution offers scalable Cove-hosted cloud storage, there is no detailed information available on its cloud-native data processing front end, which could be a concern for some users.
When tenants are provisioned in the system, they are physically tied to a single Cove cloud region. This lack of geo-distributed multiple-region service delivery options can be a limitation for businesses requiring high availability and disaster recovery across multiple regions.
Although long-term retention is available for up to 10 years, the process of data rollups introduces the risk of unintentional data loss when collapsing and compacting backups. This could potentially compromise data integrity over extended periods.
The recovery testing and standby image capabilities are available only for Windows-based OSs, limiting the solution’s applicability for environments running other OSs.
While source-side data is encrypted before transit, the encryption algorithm used is not FIPS compliant, which may be a concern for organizations with stringent security requirements.
Although hypervisor-level backups are technically supported, they do not offer the same level of granular item-level recoverability as in-guest agent-based backups, leading to an inconsistent user experience.
All data reduction capabilities, such as de-dupe and compression, are performed on the source side and scoped to the agent performing the backup. This may limit the overall efficiency of data reduction across larger, more complex environments.
The solution offers limited data immutability of 30 days with Cove Fortified Copies, which may not meet the needs of organizations requiring longer immutability periods for compliance and security purposes.
Purchase Considerations
While Cove is designed to be user-friendly, initial training for staff is highly recommended. This training will help users fully leverage the solution’s capabilities and ensure that they are comfortable with the various features and functionalities. Cove offers comprehensive training resources and support to assist with this process.
While the solution offers robust security measures such as non-FIPS compliant AES 256-bit encryption and mandatory multifactor authentication, it is important to verify that these features meet your organization’s specific compliance requirements. Additionally, assess the solution’s data immutability capabilities and ensure that they align with your regulatory needs, especially if you require longer immutability periods for compliance purposes.
Assessing how well Cove integrates with your existing IT infrastructure is advised. This includes evaluating the solution’s compatibility with your current backup and recovery processes, as well as its ability to integrate with other IT management tools. Cove provides APIs and scripting options for integration, but it is important to ensure that these capabilities meet your specific needs.
Cove is versatile, serving a range of market segments. It is well-suited for MSPs, SMBs, and large enterprises looking for efficient, scalable, and secure data protection solutions. The solution is best categorized as a Windows-optimized backup solution, covering various industries without a narrow vertical focus. It excels in environments with distributed workforces and diverse data protection needs, including on-premises, cloud, and hybrid setups.
Sonar Chart Overview
N-able is positioned on the outer edge of the Challenger circle, moving toward becoming a competitive Challenger. This positioning reflects its emerging but promising capabilities in the cloud-native data protection market. The solution’s forward movement toward improvement along a feature play axis indicates its focus on enhancing specific technical aspects and unique features rather than providing a broad platform. Cove’s architecture, which includes direct-to-cloud backups, efficient data de-dupe, and comprehensive recovery options, demonstrates its potential to address specific customer needs effectively and improve its competitive stance in the market.
Rubrik: Rubrik Security Cloud
Solution Overview
Rubrik’s Cloud-Native Protection offers robust data security and management across various cloud environments through its Rubrik Security Cloud (RSC). RSC is a comprehensive SaaS platform designed for cyber resilience across enterprise, cloud, and SaaS applications, built on a zero-trust architecture and leveraging ML. It automates data policy management, safeguards sensitive data, provides data threat analytics, and orchestrates rapid recovery. It supports AWS, Azure, and GCP, with plans for Oracle Cloud.
Key features include a serverless architecture, unified data management across multicloud environments, automated global protection via SLA Domains, encrypted and immutable backups, rapid recovery capabilities, and advanced cyber posture functionalities. The serverless design minimizes overhead and complexity, allowing seamless scalability and reduced costs.
RSC employs SLA Domains to automate global data protection, ensuring consistent policies without manual intervention. It provides encrypted, immutable backups protected by multifactor authentication, ensuring reliable recovery points. Rapid recovery for VMs, databases, and object stores, along with granular search and recovery, minimizes downtime.
The solution includes storage tiering to reduce long-term storage costs and advanced cyber posture capabilities for identifying sensitive data and detecting anomalies. It also offers logical air-gapping via Rubrik Cloud Vault for enhanced security against cyber threats. These features make firm’s Cloud-Native Protection a comprehensive solution for data security and operational resilience.
Strengths
RSC offers advanced security, comprehensive recovery options, and cost-effective data management.
It employs industry-standard AES-256 for both data-at-rest and data-in-transit encryption, ensuring robust security. The platform supports BYOK, allowing customers to manage their own encryption keys for added control. Additionally, it features key rotation and rekeying processes, enhancing security by regularly updating encryption keys and limiting the amount of data protected by a single key.
It excels in providing granular recovery options across various data types and environments. It supports file and object-level recovery, bare metal image recovery, which allows for the restoration of entire system images, ensuring comprehensive recovery in case of severe data loss. The solution offers recovery capabilities for application data, databases, and SaaS records, ensuring BC across various platforms. RSC supports the recovery of VMs and containerized applications, catering to modern cloud-native architectures.
The vendor delivers comprehensive data protection and cyber resilience across multicloud, hybrid cloud, and SaaS environments within a single SaaS platform. This unified approach simplifies data management and ensures consistent protection policies across all environments. RSC continuously monitors for suspicious activity, detects over-privileged users, and proactively identifies sensitive data. These features, combined with its Data Security Posture Management (DSPM) capabilities, enhance the platform’s ability to minimize the impact of cyberattacks.
Challenges
RSC lacks native protection for PostgreSQL, which is expected to be released later this year. It currently does not offer advanced data movement optimization techniques such as LAN or WAN optimization. WAN and LAN optimization is built to ensure fast data transfer between on-premises resources. This can impact the efficiency of data transfers, particularly for large datasets operating over WANs. This optimization is not necessary for transferring data within the cloud as cloud native snapshots reside within the cloud. Additionally, the platform does not support cloud seeding, which could be a limitation for organizations looking to expedite the initial data transfer to the cloud.
While RSC provides data compression as it is written to disk, it does not support de-dupe in its cloud-native protection model. While de-dupe is a critical feature for reducing storage costs and improving backup efficiency, Rubrik Cloud Native Protection leverages incremental snapshots. After the initial full backup, it backs up the changed data (delta) only incrementally. To leverage de-duple, customers must deploy Rubrik’s non-cloud-native Cloud Data Management (CDM) appliance, which may not be ideal for those seeking a purely cloud-native solution.
Purchase Considerations
When considering RSC, it is essential to understand the feature disparity between RSC and firm’s non-cloud-native CDM appliance. While RSC offers a comprehensive, cloud-native solution with strong encryption, automated global protection, and advanced cyber resilience capabilities, it lacks certain features available in the CDM appliance. For instance, it does not support de-dupe due to cloud considerations, whereas the CDM appliance provides robust de-dupe capabilities, which can significantly reduce storage costs and improve backup efficiency.
Prospective buyers should evaluate their specific needs and consider whether the advanced features of the CDM appliance, such as de-dupe and potentially more optimized data movement techniques, are critical for their environment.
Additionally, organizations may require professional services and training to fully leverage RSC’s extensive capabilities. Ensuring that the vendor’s support and maintenance services align with your operational requirements is crucial for a smooth deployment and ongoing management.
RSC serves a range of industries, geographies, and company sizes, making it a versatile solution. It is for organizations with complex multicloud and hybrid environments that require robust data protection and cyber resilience capabilities. The platform’s comprehensive features make it for industries with stringent data security and compliance requirements, such as finance, healthcare, and large enterprises.
Sonar Chart Overview
The company is positioned as a disruptive Challenger, moving toward becoming an early stage Leader. This positioning reflects its innovative approach to cloud-native data protection, leveraging zero-trust principles and machine learning to secure data across enterprise, cloud, and SaaS applications. The platform’s fast movement toward improvement along the innovation play axis reflects its focus on introducing significant new features and capabilities, such as anomaly detection, threat hunting, and cyber recovery simulations. Vendor’s rapid development and comprehensive security measures demonstrate its potential to significantly impact the market and enhance its competitive stance.
Veritas: Alta
Solution Overview
Veritas Technologies stands out in multicloud data management, boasting one of the largest customer bases, including most of the Fortune 100 companies. Alta, its cloud-native data management platform, integrates services like data protection, application resiliency, compliance, and governance. It is a suite of solutions, not a single product, with key components such as Alta Data Protection, Alta View, and Alta Copilot.
The platform uses AI-powered automation, flexible recovery options, and cloud-native storage to provide cost-effective, resilient, and autonomous data protection across any cloud environment. Built on the Veritas Cloud Scale Technology architecture, it enhances scalability, efficiency, and security using modern IT techniques like containerization, Kubernetes orchestration, and microservices.
Alta Data Protection offers extensive protection for cloud workloads, supporting over 800 data sources, more than 100 OSs, and over 40 cloud platforms. Alta View is a centralized console that unifies the management of a customer’s data estate across edge, core, and cloud environments, simplifying backup management and providing comprehensive analytics and insights.
Alta Copilot, an AI-powered assistant, uses generative AI and retrieval-augmented generation (RAG) to simplify data management tasks, offering self-serve support, dynamic data visualization, and actionable guidance. This unified platform supports diverse cloud infrastructures and features advanced AI-based anomaly detection and automated orchestration, distinguishing it from more fragmented solutions.
Strengths
The company offers comprehensive cyber resilience, recovery options, and cost-effective data management. The platform uses a cloud-native data plane architecture optimized for multicloud infrastructures, leveraging Kubernetes for efficient service delivery. This ensures seamless integration and operation across various cloud environments, enhancing flexibility and performance.
Alta View, a unified console, provides centralized visibility and control across multiple cloud providers, ensuring high availability and simplifying operations. The platform supports infinite retention and access to managed cloud resources, ensuring robust business continuity. The Alta Recovery Vault offers fully managed, cloud-based data retention and isolation services, supporting long-term storage and quick recoverability.
Security is enhanced with end-to-end encryption for data in-flight and at rest, including options for BYOK and rotating keys. The platform supports fine-grained recoverability for endpoints, servers, VMs, SaaS applications, and cloud environments.
Advanced data movement optimization features such as bandwidth management and cloud seeding minimize resource usage and improve data transfer efficiency. Alta also offers comprehensive data management and analytics capabilities, including reporting, eDiscovery, FinOps, and predictive analytics, providing valuable insights and optimizing data management strategies.
Global de-dupe and compression techniques maximize storage capacity efficiency, significantly reducing storage costs. Cyber resilience is further enhanced with features like data immutability, malware detection, admin and data anomaly detection, adaptive MFA/MPA authentication, and automated remediation, protecting vs. ransomware and other cyber threats.
Challenges
One of the primary challenges associated with Alta is its inherent complexity. The platform’s comprehensive nature, which integrates a wide array of services, features, and capabilities can make deployment and ongoing management quite intricate. Organizations may need to invest significant time and resources to fully understand and leverage the platform’s capabilities. This complexity can be particularly daunting for smaller IT teams or organizations without extensive experience in managing sophisticated data protection and management solutions. The need for specialized knowledge and expertise to configure, optimize, and maintain the platform effectively can pose a barrier to its adoption and efficient use.
While Alta offers substantial benefits in terms of data protection, scalability, and operational efficiency, similar to those of other enterprise-class solutions, the investment required can be substantial if there is no IT expertise available. The initial costs for deploying the platform, including licensing fees, infrastructure setup, and potential professional services, can be high. Additionally, ongoing costs related to maintenance, updates, and support services can add to the financial burden. For smaller organizations or those with limited budgets, these costs might be prohibitive, potentially limiting the value of Alta’s advanced features and capabilities. Evaluating the total cost of ownership, including both direct and indirect expenses, is crucial for organizations considering this solution.
Careful planning, resource allocation, and a commitment to continuous learning and optimization are essential for successfully implementing and leveraging Alta.
Purchase Considerations
Organizations considering Alta should ensure they have the necessary expertise or access to professional services to deploy, manage, and operate the platform effectively. Training and support are crucial to fully leverage the platform’s capabilities. Additionally, evaluating the total cost of ownership, including up front solution acquisition costs, cloud-native infrastructure consumption, and potential savings from optimization and reduced operational overhead, is essential for making an informed purchase decision.
Alta is a general-purpose solution designed to serve a range of industries, including finance, healthcare, and manufacturing. It is for enterprises with complex, multicloud environments that require robust data protection, compliance, and resiliency solutions. The platform’s flexibility and scalability make it ideal for organizations looking to streamline their data management processes and enhance their cybersecurity posture.
Sonar Chart Overview
Alta is positioned as a competitive Leader, moving toward becoming a market-dominant Leader. This positioning reflects its robust capabilities in cloud-native data protection, including AI-powered automation, flexible recovery options, and comprehensive workload support across hybrid, multicloud, and on-premises environments. The solution’s forward movement toward improvement of a balanced play indicates its focus on both innovation and maturity, and both features and platform. Alta’s rapid development and integration of advanced data protection features, such as ransomware resiliency and automated data classification, demonstrate its potential to dominate the market.
6. Near-Term Roadmap
Cloud-native data protection is rapidly evolving to meet the demands of modern enterprises that are increasingly reliant on modern public and private cloud infrastructures. This evolution is driven by several key trends and technological advancements that are shaping the future of data protection in the cloud.
As cloud-native data protection solutions evolve, they are incorporating advanced security features such as malware and ransomware protection, automated remediation, and AI-enriched data management optimizations. These measures are emerging as new feature capabilities for protecting sensitive data and ensuring compliance with industry regulations.
Cloud-native data protection solutions are designed to scale seamlessly with the growth of an organization’s data. They offer flexible deployment models, including SaaS, hybrid, and on-premises options, to meet diverse business needs. Solutions like Clumio and HYCU R-Cloud provide scalable and flexible data protection capabilities, enabling organizations to protect a wide range of data sources across different environments.
The pay-as-you-go pricing models and capacity bundles offered by cloud-native data protection solutions help organizations manage costs effectively. Solutions like Backblaze B2 Cloud Storage provide affordable and predictable pricing, making it easier for enterprises to budget for data protection without incurring unexpected expenses.
Modern data protection solutions are integrating advanced data management and analytics capabilities. These features enable organizations to gain insights into their data usage, identify potential security threats, and optimize their data protection strategies. Solutions like Commvault Cloud Platform and Veritas Alta leverage AI and ML to provide proactive threat detection and data governance, enhancing overall data security and operational efficiency.
The future of cloud-native data protection is characterized by increased security, scalability, and flexibility. As organizations continue to adopt hybrid and multicloud strategies, the demand for advanced data protection solutions that can seamlessly integrate with diverse cloud environments will grow. The emphasis on sustainable computing practices and the rise of edge and serverless computing will further drive innovation in this space, ensuring that data protection solutions remain robust, efficient, and environmentally conscious.
7. Analyst’s Outlook
The cloud-native data protection market is experiencing significant growth, driven by the increasing adoption of cloud services and the need for robust data protection solutions. This growth is fueled by the rising demand for comprehensive, all-in-one native systems that simplify monitoring, detecting, and acting on cloud environments and workloads. These platforms are essential for accelerating threat hunting, addressing runtime threats, and ensuring compliance.
The market is evenly distributed between platform solutions and feature-focused solutions, which all offer unique differentiators to data protection and security. These solutions integrate a range of functionality including threat detection, predictive analytics, and data preservation into a single solution. This integration helps reduce the complexity and cost associated with managing multiple tools and vendors. Professional services also play a crucial role, providing organizations with the expertise needed to implement and manage these platforms effectively.
Understanding the landscape begins with recognizing the importance of a unified platform that can address multiple aspects of data protection and security. Key players in this space include mature, well-known vendors focused on transforming existing best-of-breed solutions and new entrants catering to niche features and use cases, each offering unique strengths and capabilities.
For IT decision-makers considering the adoption of cloud-native data protection solutions, begin by evaluating your organization’s specific data protection requirements including compliance, scalability, and integration needs. Consider the types of workloads and environments you need to protect. Compare the offerings of both mature and new vendors. Look for solutions that offer comprehensive protection, ease of use, and flexibility to address your unique business requirements. Implement pilot programs to test the chosen solutions in your environment. This will help you understand the practical implications of each solution and identify any potential challenges.
Finally, consider using professional services to ensure a smooth implementation and to gain insights into best practices for managing and optimizing your chosen cloud-native data protection platform.
8. Report Methodology
A GigaOm Sonar report analyzes emerging technology trends and sectors, providing decision-makers with the information they need to build forward-looking, rewarding IT strategies. Sonar reports provide an analysis of the risks posed by the adoption of products that are not yet fully validated by the market or available from established players.
In exploring bleeding-edge technology and addressing market segments still lacking clear categorization, Sonar reports aim to eliminate hype, educate about technology, and equip readers with insight that allows them to navigate different product implementations. The analysis highlights core technologies, use cases, and differentiating features, rather than drawing feature comparisons. This approach is taken mostly because the overlap among solutions in nascent technology sectors can be minimal. In fact, product implementations based on the same core technology tend to take unique approaches and focus on narrow use cases.
The Sonar report defines the basic features that users should expect from products that satisfactorily implement an emerging technology, while taking note of characteristics that will have a role in building differentiating value over time.
In this regard, readers will find similarities with the GigaOm Key Criteria and Radar reports. Sonar reports, however, are specifically designed to provide an early assessment of recently introduced technologies and market segments. The evaluation of the emerging technology is based on:
Core technology: Table stakes
Differentiating features: Potential value and key criteria
Over the years, depending on technology maturation and user adoption, a particular emerging technology may either remain niche or evolve to become mainstream (see Figure 2). GigaOm Sonar reports intercept new technology trends before they become mainstream and provide insight to help readers understand their value for potential early adoption and the highest ROI.

Figure 2. Evolution of Technology
9. About GigaOm
It provides technical, operational, and business advice for IT’s strategic digital enterprise and business initiatives. Enterprise business leaders, CIOs, and technology organizations partner with GigaOm for practical, actionable, strategic, and visionary advice for modernizing and transforming their business. GigaOm’s advice empowers enterprises to successfully compete in an increasingly complicated business atmosphere that requires a solid understanding of constantly changing customer demands.
GigaOm works directly with enterprises both inside and outside of the IT organization to apply proven research and methodologies designed to avoid pitfalls and roadblocks while balancing risk and innovation. Research methodologies include but are not limited to adoption and benchmarking surveys, use cases, interviews, ROI/TCO, market landscapes, strategic trends, and technical benchmarks. Our analysts possess 20+ years of experience advising a spectrum of clients from early adopters to mainstream enterprises.
GigaOm’s perspective is that of the unbiased enterprise practitioner. Through this perspective, the firm connects with engaged and loyal subscribers on a deep and meaningful level.














 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter

