Attackers Steal Data from Thunderbolt-Equipped Windows or Linux Computers
In five minutes
This is a Press Release edited by StorageNewsletter.com on May 14, 2020 at 2:44 pmThis report, published on April 17, 2020, was written by Björn Ruytenberg Eindhoven University of Technology.
Breaking Thunderbolt Protocol Security: Vulnerability Report

Thunderspy targets devices with a Thunderbolt port. If your computer has such a port, an attacker who gets brief physical access to it can read and copy all your data, even if your drive is encrypted and your computer is locked or set to sleep.
Thunderspy is stealth, meaning that you cannot find any traces of the attack. It does not require your involvement, i.e., there is no phishing link or malicious piece of hardware that the attacker tricks you into using. It works even if you follow best security practices by locking or suspending your computer when leaving briefly, and if your system administrator has set up the device with Secure Boot, strong BIOS and OS account passwords, and enabled full disk encryption. All the attacker needs is 5 minutes alone with the computer, a screwdriver, and some easily portable hardware.
We have found 7 vulnerabilities in Intel’s design and developed 9 realistic scenarios how these could be exploited by a malicious entity to get access to your system, past the defenses that Intel had set up for your protection.
We have developed a free and open-source tool, Spycheckhttps://thunderspy.io/files/Spycheck-Windows-20200511.zip, to determine if your system is vulnerable. If it is found to be vulnerable, Spycheck will guide you to recommendations on how to help protect your system.
Thunderspy PoCs in Action
Cloning user-authorized device identities to arbitrary attacker devices
Thunderspy enables creating arbitrary Thunderbolt device identities and cloning user-authorized Thunderbolt devices, even in the presence of security levels pre-boot protection and cryptographic device authentication.
Permanently disabling Thunderbolt security and future firmware updates
Thunderbolt Controller Firmware Patcher (tcfp), a firmware patching toolkit we have developed, enables disabling Thunderbolt security without requiring access to the victim system BIOS or OS. Moreover, tcfp enables disabling Thunderbolt security covertly – without reflecting the new state in the BIOS.
SPIblock, another tool we have developed, allows programming on-flash write protection. Specifically, this includes configuring SPI flash to employ an irrevocable, read-only state. When combined with tcfp, it allows to permanently, and covertly, disable Thunderbolt security and block all future firmware updates.
Full Summary
Thunderbolt is a high-bandwidth interconnect promoted by Intel and included in laptops, desktops, and other systems. Being PCIe-based, Thunderbolt devices possess Direct Memory Access (DMA)-enabled I/O. In an evil maid DMA attack, where adversaries obtain brief physical access to the victim system, Thunderbolt has been shown to be a viable entry point in stealing data from encrypted drives and reading and writing all of system memory. In response, Intel introduced Security Levels, a security architecture designed to enable users to authorize trusted Thunderbolt devices only. To further strengthen device authentication, the system is said to provide “cryptographic authentication of connections” to prevent devices from spoofing user-authorized devices.
We present Thunderspy, a series of attacks that break all primary security claims for Thunderbolt 1, 2, and 3.
So far, our research has found the following vulnerabilities:
1 Inadequate firmware verification schemes
2 Weak device authentication scheme
3 Use of unauthenticated device metadata
4 Downgrade attack using backwards compatibility
5 Use of unauthenticated controller configurations
6 SPI flash interface deficiencies
7 No Thunderbolt security on Boot Camp
These vulnerabilities lead to 9 practical exploitation scenarios. In an evil maid threat model and varying Security Levels, we demonstrate the ability to create arbitrary Thunderbolt device identities, clone user-authorized Thunderbolt devices, and finally obtain PCIe connectivity to perform DMA attacks. In addition, we show unauthenticated overriding of Security Level configurations, including the ability to disable Thunderbolt security entirely, and restoring Thunderbolt connectivity if the system is restricted to exclusively passing through USB and/or DisplayPort. We conclude with demonstrating the ability to permanently disable Thunderbolt security and block all future firmware updates.
All Thunderbolt-equipped systems shipped between 2011-2020 are vulnerable. Some systems providing Kernel DMA Protection, shipping since 2019, are partially vulnerable. The Thunderspy vulnerabilities cannot be fixed in software, impact future standards such as USB 4 and Thunderbolt 4, and will require a silicon redesign. Users are therefore strongly encouraged to determine whether they are affected using Spycheck, a free and open-source tool we have developed that verifies whether their systems are vulnerable to Thunderspy. If it is found to be vulnerable, Spycheck will guide users to recommendations on how to help protect their system.
Thunderbolt: A Closer Look
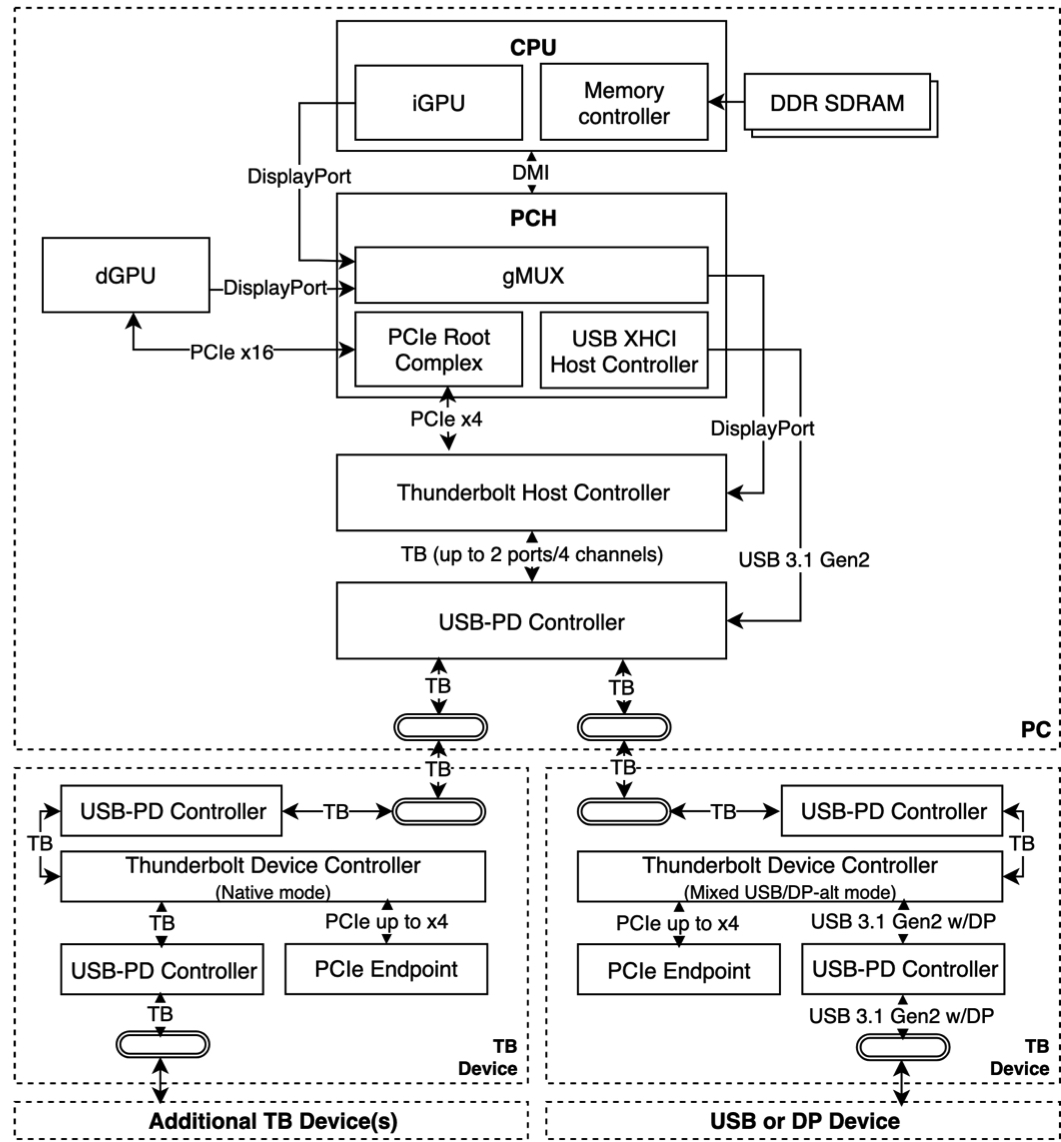
Thunderbolt controllers can operate in either Host Mode or Endpoint Mode. In Host Mode, Thunderbolt controllers connect to the system using a bare-metal PCIe interface. Pictured above is an example PCIe topology in more detail. As can be seen, in this situation, the PCH exposes a PCIe x4 link to a Thunderbolt 3 controller. USB support is implemented using two auxiliary components. While the PCH provides a USB 3.1-compliant host controller, a third-party IC extends USB signaling with Power Delivery support, and concurrently multiplexes between Thunderbolt and USB signaling as appropriate.
To this end, Thunderbolt 3 defines silicon
that can dynamically switch between the following PHY modes:
• USB passthrough mode. If a USB device is plugged in, the PCH USB host controller is activated. In this mode, the Thunderbolt 3 port operates as a USB 3.0 Type C interface, that is, without DisplayPort (DP) alt-mode support.
• Mixed USB/DisplayPort mode. Enables support for “mixed mode” devices, such as USB Type C hubs with DisplayPort sinks. In this mode, the Thunderbolt 3 port operates as a USB 3.1 Gen 2 Type C interface supporting DP alt-mode.
• Native Thunderbolt mode. If a Thunderbolt device is plugged in, the Thunderbolt silicon enables two full-duplex links to the device providing a per-link throughput between 10 to 20 Gb/s, depending on the negotiated Thunderbolt version. The device, operating in Endpoint Mode, demultiplexes these links to a maximum of four PCIe lanes and two four-lane DP streams.
Thunderbolt devices can be daisy-chained. Aside from sharing one port between multiple devices, daisy-chaining allows for a variety of topologies with mixed controller configurations, such as illustrated in in the figure. Contrary to USB, Thunderbolt is a proprietary connectivity standard. Device vendors are required to apply for Intel’s Thunderbolt developer program, in order to obtain access to protocol specs and the Thunderbolt hardware supply chain. In addition, devices are subject to certification procedureshttps://thunderbolttechnology.net/developer-application/new before being admitted to the Thunderbolt ecosystemhttps://thunderbolttechnology.net/products.
Who discovered Thunderspy?
The Thunderspy vulnerabilities have been discovered and reported by Björn Ruytenberg.
Disclosure Timeline
We disclosed vulnerabilities 1-5 to Intel on February 10. They wrote on March 10 that their engineering team confirmed the vulnerabilities, and that vulnerabilities 3-5 were new to them. After further research we disclosed vulnerability 6, which Intel confirmed on March 17.
In our first email we asked Intel to promptly notify affected parties, in coordination with us. However, Intel did not take any action and finally, after several email exchanges, listed only 5 parties whom they would inform. We then sent them a list of other parties we had identified as affected, including 11 OEMs/ODMs and the Linux kernel security team. Eventually they notified us that they informed some parties on March 5 about the vulnerabilities and upcoming disclosure, without giving us details of what this information consisted of and whom exactly they contacted. We reached out to several more parties after realizing that they had been skipped by Intel.
Finally, we informed Apple of vulnerability 7 on April 17.









 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter

