Data Sanitization: Policy Vs. Reality
Exposing discrepancies between data sanitization policy creation and execution
This is a Press Release edited by StorageNewsletter.com on March 19, 2020 at 2:19 pmThis survey was published on February 20, 2020 by Blancco Technology Group.
Data Sanitization: Policy vs. Reality
Exposing the discrepancies between data sanitization policy creation and execution
Do you have data sanitization (e.g. physical destruction, overwriting, formatting a drive, etc.)
policy in place in your organization?
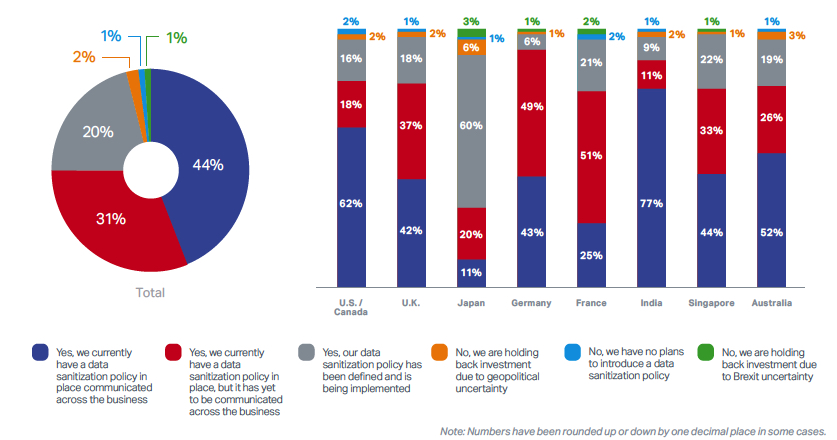
Seven Key Data Sanitization Best Practices:
1. If using a third-party ITAD vendor, ask them to provide a full chain of custody for your end-of-life devices, from pickup to
transport. Ensure you receive a certificate of destruction for each asset.
2. Ensure your data sanitization policy includes all IT assets, including smartphones, tablets, PCs, servers, loose drives,
removable media virtual machines, etc.
3. Define SLAs for ensuring devices are sanitized immediately at end-of-life, preferably within 24 hours, to minimize risk.
4. Ensure no assets leave your enterprise or data center environment with sensitive data on them. Erase devices onsite
and ensure that you receive a tamper-proof certificate of erasure. This includes devices that are repurposed within the
organization (e.g. when an employee leaves) and assets that leave the organization (for donation, resale or recycling).
5. Create a clear plan for communicating your data sanitization policy to employees on a regular basis. Plan to provide training
as needed and ensure that someone has ownership of this process.
6. Ensure each person and department’s involvement in each data sanitization process is clearly defined, with specific roles and responsibilities outlined for redeployment, resale, recycling, donation, etc.
7. Conduct regular internal audits. By doing so, you can determine if your policies are executed properly across every department employee and even your partners and vendors.
Conclusion
Although many enterprises have shown commitment when it comes to creating data sanitization policies, clearly not enough has been done. Organizations must look at their current data security policies, particularly around data sanitization, and determine if they are comprehensive enough to avoid potentially hidden risks, such as lack of employee awareness or gaps in decommissioning processes (leaving equipment unsanitized onsite, not addressing all assets, not having oversight from the compliance team, etc.). Only by doing so will the 96% of enterprises that say they have a data sanitization policy close the gap between data sanitization policy and reality. This is an especially important message for the 89% of organizations that say their data sanitization policy is fewer than 12 months old. With such fresh policies, it’s understandable that not every issue has been covered yet, but it’s also important to ensure these policies are comprehensive enough to cover such issues as ownership, communication and chain of custody moving forward.









 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter

