Dell EMC Launches Cyber Recovery Software
Software and services to isolate critical data from ransomware and cyber attacks
This is a Press Release edited by StorageNewsletter.com on October 23, 2018 at 2:27 pmDell EMC, part of Dell Technologies, announced Cyber Recovery software, along with Cyber Recovery Services designed to help provide a last line of data protection defense against ransomware and destructive cyber attacks.
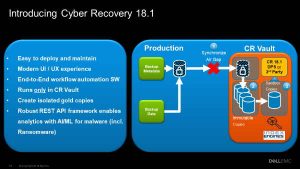
This software includes automation, workflow and security analytics tools to ensure gold copies of critical data are isolated yet available so business processes can be resumed as quickly as possible in the event of a destructive cyber attack.
Cyber attacks have become a common occurrence, the worst of which often result in extended downtime that can bring business operations to a standstill for days and even weeks – costing millions of dollars. While many large organizations have strong cyber security and anti-malware detection capabilities in place, the impact of not being able to recover business processes and data in the event of a successful ransomware or destructive cyber attack can be devastating.
Click to enlarge
“Malicious insiders and sophisticated cyber attackers, especially those that employ ransomware, are known to deliberately target data protection and backup infrastructure,” said Beth Phalen, president, data protection, Dell EMC. “We take a layered approach to data protection within the portfolio and with our Dell EMC Cyber Recovery software and Services, helping ensure true data isolation and a last line of data protection defense for business-critical data from a variety cyber threats.”
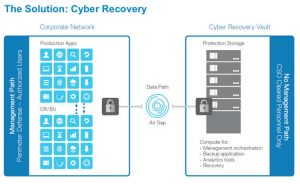
Cyber Recovery is a software that integrates with the company’s Data Domain protection storage hardware. It provides a solution that combines the benefits of data isolation and business continuity to help minimize the impact of a cyber attack, while providing a faster and higher likelihood of success in the recovery of critical data and systems.
Click to enlarge
Cyber Recovery automates the retention of isolated secure copies of critical data within a Cyber Recovery Vault (CR Vault), removing them from the attack surface. Serving as the ideal test bed, the CR Vault allows customers to perform security analytics on the retained data without having to perform a restore and potentially activating malware that may be present in the protected dataset. A REST API automation framework provides integration with security analytics software packages such as Index Engines CyberSense which applies over 40 heuristics to determine indicators of compromise.
Click to enlarge
Cyber Recovery Services
The company also offers Cyber Recovery Services focused on providing a solution which is tailored to the customer’s exact data protection and cyber security requirements.
This is accomplished through an expanded set of services including:
-
Workshop: During this one-day workshop, consultants share the firm’s practices for business resiliency with a strong focus on cyber recovery.
-
Advisory: The advisory service builds on the Workshop by adding development of a high level cyber recovery strategy. The customer’s current and desired state is analyzed to create a tailored strategy for cyber recovery preparedness.
-
Advisory and roadmap: The advisory and roadmap builds on the advisory service with a deeper dive into customer’s cyber recovery strategy to recommend an optimized implementation roadmap. This includes developing a cyber recovery maturity model report, which benchmarks the customer’s current state against industry best practices. Also included is a critical materials workshop and information session to collect data on the customer’s applications to understand criticality to the business. These considerations will help drive recommendations of data and applications which should be protected by the Cyber Recovery Vault.
-
Deployment: New deployment services help maximize the capabilities of Cyber Recovery solutions. They can be added to the ProDeploy Enterprise suite or purchased separately and are available in two variations to fit customer needs.
-
Implementation: The company’s services can also customize the implementation of the Cyber Recovery Solution to account for a variety of additional use cases. This can include hardening of additional firm’s technology, developing detailed operational procedures and implementing custom dashboards and reporting.
Click to enlarge
Cyber Recovery software is available through the company at no additional cost with purchase of Data Domain (DDOS 6.0.x and higher). Cyber Recovery Services are available.
Bob Bender, CTO, Founders Federal Credit Union, said: “Financial institutions are among the most targeted organizations for cyber attacks and our responsibility is to ensure the highest levels of security for our members and the financial assets they entrust us with. All it takes is for one successful intrusion or ransomware attack to seriously disrupt any business and if the bad guys are smart enough to know where your backups are, you’re left with no protection. Dell EMC Cyber Recovery helps my team isolate all of our critical data off-network, giving us confidence in our business resilience in the event of a worst-case cyber attack scenario.”
Christophe Bertrand, senior analyst, ESG, said: “The most effective plans for cyber threat resilience must include provisions to protect and isolate the data protection infrastructure. By design data protection systems are architected on the same networks as production systems and are therefore part of the potential attack surface. Dell EMC offers a smart solution that employs an air-gapped Cyber Recovery Vault, along with automated software that helps isolate, analyze and recover an organization’s critical data so business can resume in the event of a cyber intrusion or ransomware attack.“
Tim Williams, CEO, Index Engines, Inc., said: “No one can guarantee 100% protection against cyber attacks. When attacks occur, and data is corrupted, it is important to quickly identify the attack vector and replace bad files to avoid business interruption. Dell EMC’s Cyber Recovery solution has met this challenge by integrating CyberSense from Index Engines. CyberSense’s ransomware and data integrity analytics incorporates a machine learning model that will detect if your data has been successfully attacked with a great degree of certainty. Once detected, its forensic analysis tools will help determine the compromised user account and the suspect malware. With CyberSense, a cyberattack can be minimized and organizations can recover with confidence in as little as one backup cycle.“
Resources:
Direct2DellEMC blog: Dell EMC Strengthens Last Line of Data Protection Defense Against Cyber Attacks with New Cyber Recovery Software
InFocus Blog: 4 Key Considerations for Your Cyber Recovery Strategy
Cyber Recovery Software DS
Cyber Recovery Services DS
Cyber Recovery Infographic
















 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter


