Storage and Data Protection Survey
Feedback from storage, backup and IT infrastructure leaders in Fortune 500 enterprises
This is a Press Release edited by StorageNewsletter.com on September 23, 2024 at 2:01 pmThis market report was written by Continuity Software Ltd.
Storage and Data Protection Survey Results
2025 Priorities for Storage & IT Infrastructure Teams
In a survey we ran throughout May-August 2024, we compiled feedback from storage, backup and IT infrastructure leaders in Fortune 500 enterprises. The purpose of this survey was to understand their plans and priorities for managing configuration
of storage and backup environments, staying on top of configuration changes, deploying new cyber recovery capabilities, as well as navigating audit compliance requirements.
Key findings
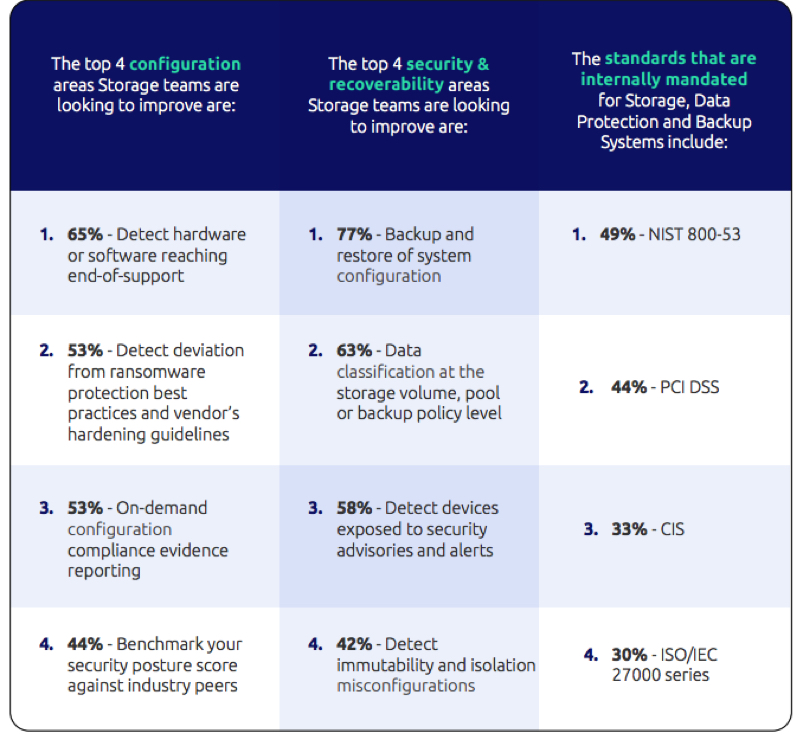
Configuration
Detect hardware or software reaching end-of-support
As storage and backup systems reach end-of-support, vendors stop providing updates, patches, and technical support. This leaves your mission-critical systems vulnerable to security risks. By proactively detecting and addressing end-of-support systems, you can ensure continuous security posture and data protection – while improving system reliability.
Detect deviation from ransomware protection best practices and vendor’s hardening guidelines
As ransomware threats grow, organizations are increasingly looking at ways to secure their storage and backups, yet many still feel vulnerable. Key strategies include implementing immutable backups, secure snapshots, anomaly detection, user behavior analysis, multi-factor authentication (MFA), 2-person integrity controls, and secure time synchronization. Additionally, it’s crucial to rigorously follow vendor-recommended hardening guidelines, such as enforcing encrypted communications, account lockout policies, and the use of robust cipher suites and hashing algorithms, to ensure comprehensive protection.
On-demand configuration compliance evidence reporting
Many organizations still rely on manual processes to prove compliance during audits, recognizing the need for improvement. Manual evidence gathering is cumbersome, time-consuming, and lacks repeatability. Automation can streamline compliance validation and evidence production, whether it’s for data at-rest encryption or TLS configurations. By automating these tasks, organizations can operate at scale, efficiently manage diverse systems, and reduce dependence on individual team members, ultimately improving accuracy and consistency in compliance efforts.
Benchmark your security posture score vs. industry peers
Survey participants are keen on benchmarking their security posture vs. industry peers, probably because it provides a clear understanding of where they stand in terms of security maturity. By comparing their scores, they can identify gaps, prioritize improvements, and justify investments in security initiatives. This benchmarking also fosters a competitive spirit, driving organizations to achieve higher standards, and offers reassurance that their practices align with or exceed industry norms, ultimately enhancing overall data protection and compliance.
Security & Recoverability
Backup and restore of system configuration
In conjunction with data backup, it is crucial to also regularly backup device and system configurations. System configuration includes settings, policies, and operational parameters, and are critical to the proper functioning and performance of storage and backup infrastructure. In the event of a system failure, corruption, or cyberattack, having a backup of these configurations ensures that the system can be quickly and accurately restored to its operational state; minimizing downtime and avoiding the complexities of manual reconfiguration. This capability not only safeguards the integrity and reliability of the storage and backup environment
but also supports business continuity by enabling swift recovery from unexpected disruptions. Ensuring that configuration backups are part of a broader data protection strategy, and provides an additional layer of security to help organizations maintain seamless operations, even in the face of unforeseen challenges.
Data classification at the storage volume, pool or backup policy level
Data classification at the NFS share, SMB share, storage volume, storage pool, or backup policy level is crucial for enhancing data security and compliance within an organization. By categorizing data based on its sensitivity – such as personally identifiable information (PII), protected health information (PHI), or social security numbers – organizations can apply appropriate access controls, encryption, and monitoring measures tailored to the level of risk associated with each data type.
This granular approach to data classification ensures that sensitive information is protected from unauthorized access or exposure, reducing the risk of data breaches and ensuring compliance with regulatory requirements such as GDPR, HIPAA, and others.
Furthermore, by integrating data classification into backup policies, organizations can prioritize the protection of critical data, ensuring that it is securely backed up and easily recoverable in the event of data loss. This comprehensive strategy not only safeguards sensitive data across various storage and backup environments but also optimizes resource allocation and strengthens the overall security posture of the organization.
Detect devices exposed to security advisories and alerts
In recent months, multiple vulnerabilities in storage and backup solutions have been discovered and actively exploited. These include:
Veeam Backup & Replication:
- CVE-2022-26500 and CVE-2022-26501: These vulnerabilities allow remote,
- unauthenticated attackers to execute arbitrary code.
- CVE-2023-27532: This high-severity vulnerability allows attackers to bypass
- authentication and access sensitive data.
MinIO:
- CVE-2023-28432: This vulnerability allows attackers to return all environment
- variables, including sensitive information like root passwords
- CVE-2023-28434: An attacker can use crafted requests to bypass metadata bucket name checking and put an object into any bucket while processing PostPolicyBucket.
Veritas Backup Exec:
- CVE-2021-27876: This vulnerability allows unauthorized file access through the
- Backup Exec Agent.
- CVE-2021-27877: This involves improper authentication, potentially allowing
- attackers to access sensitive information.
- CVE-2021-27878: This vulnerability permits command execution, allowing
- attackers to run arbitrary commands on affected systems.
Oracle ZFS Storage Appliance:
- CVE-2020-14871: Easy-to-use, actively exploited vulnerability that allows unauthenticated attacker to compromise the system, causing high impacts to confidentiality, integrity, and availability









 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter

