WW Cyber-Recovery 2023
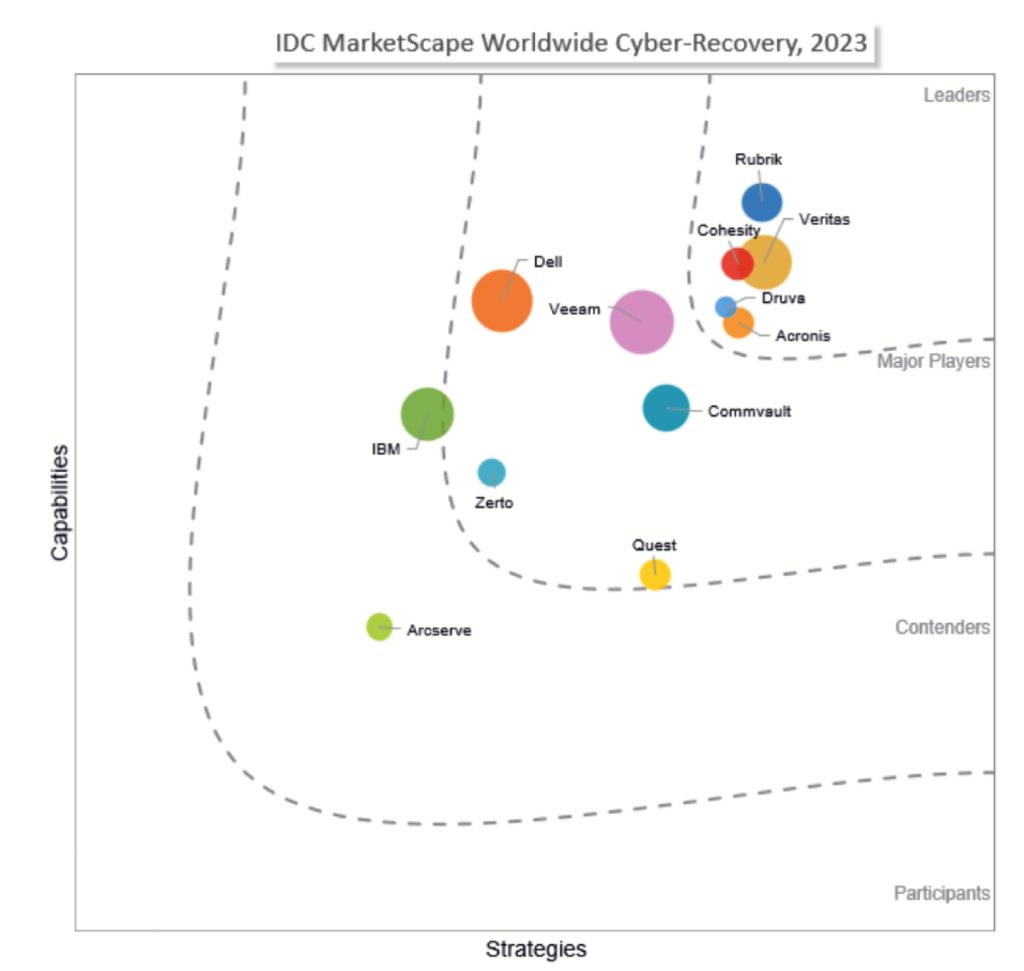
Leaders Rubrik, Cohesity, Veritas, Druva and Acronis
This is a Press Release edited by StorageNewsletter.com on November 30, 2023 at 2:01 pmThis market report, published on October 2023, was written by Phil Goodwin, Johnny Yu and Greg Macatee, analysts at IDC Corp.
IDC MarketScape: Worldwide Cyber-Recovery 2023
Vendor Assessment
IDC opinion
Cyberattack is front and center among the biggest threats faced by organizations worldwide. Cyberattackers spare no organization regardless of size, industry, geography, or political boundary. Unfortunately, there is no end in sight for cybercrime because it is simply too profitable for the perpetrators. For victims, the consequences can include lost revenue, permanently lost customers, lost employee productivity, regulatory fines, and unrecoverable data, not to mention the ransom cost itself. Perhaps worse, some organizations face shareholder lawsuits and class action lawsuits in the wake of the attack.
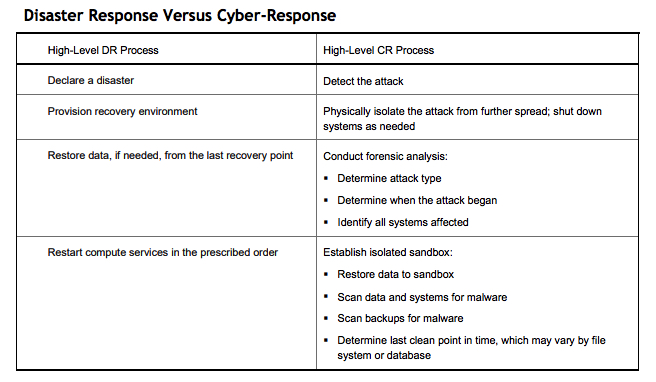
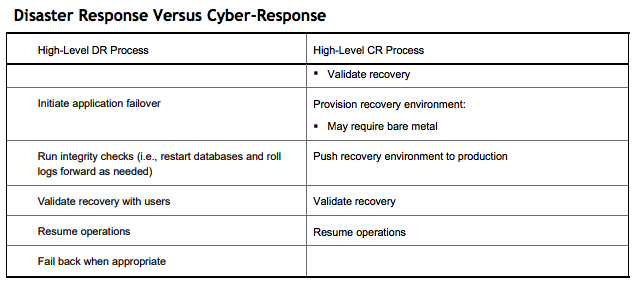
In the early days of ransomware attacks, organizations relied on data backup images to recover. As attackers became more sophisticated and comprehensive and attacks began with wiping out the backup images, IT teams began declaring disaster responses to cyberevents. However, there are important differences between DRs and cyber-recoveries. Table 1 makes the comparison. It does not attempt to capture every step of either process, but rather to illustrate that DR efforts alone are likely to yield poor results for cyberevents.
Table 1
IDC uses the U.S. National Institute of Standards and Technology (NIST) framework for cyber-resilience. This framework includes 5 “pillars”: identify, protect, detect, respond, and recover (for more information, go to www.nist.gov/cyberframework/). Fundamentally, these pillars fall into 2 categories: proactive defense and reactive recovery. To be truly cyber-resilient, organizations need “both,” but unfortunately no single vendor can supply everything. Traditional data protection tends to focus on the “respond and recover” pillars, with data security focusing on the identify, protect, and detect pillars. However, many vendors – whether rooted in data protection or data security – are moving to offer capabilities across all 5 pillars, at least for some specific capabilities.
IT leaders acknowledge no one can prevent cyberattack with absolute certainty. In fact, most agree that an attacker is going to get inside their systems sooner or later. Moreover, this research shows data exfiltration ransom events occur about 50% more often than data encryption ransom events. This is because organizations are getting better at recovering encrypted data, but there is no recovery from data exfiltration; organizational leaders decide to either pay the ransom or not. However, even though there is no recovery from exfiltration, cyber-recovery vendors can offer important capabilities to reduce the impact, such as strong data encryption and immutability.
The analysts believe cyber-resilient organizations will begin by locking down on 3 principles:
- Absolutely certain data survival: Without absolutely certain data survival, it is highly likely that the organization will be forced to pay the ransom to get its data back. It is also likely to suffer data loss, as our research shows this to be common among victims. Organizations need to know they can get their data back no matter what.
- Absolutely certain data integrity: Similarly to data survival, organizations need to know that the data they recover is accurate data. Without this, they are again relying on criminals to do the honorable thing after receiving the ransom.
- Rapid recovery with minimal data loss: Downtime is the friend of attackers and the enemy of victims. The prospect of a long recovery may drive the organization to pay the ransom, even if it has clean, recoverable data. Being able to detect the attack, quarantine it, assess the damage, and resume operations quickly mitigates any damage.
Because of the unique requirements for cyber-response (CR), IT organizations are moving quickly to implement cyber-response systems and vendors are responding to user and market needs just as quickly with rapidly evolving solutions. This dynamic market is good for IT consumers as it offers high differentiation, robust competition, and an opportunity to find a solution that closely fits the organization’s needs. This report evaluates what the analysts believe are the 12 most prominent cyber-recovery vendors. Each vendor has unique capabilities and applicable “sweet spot” scenarios. This evaluation is intended to help IT buyers differentiate between the different vendors to select the right one for their situation.
Advice for technology buyers
All of the vendors in this analysis support on-premises, hybrid cloud, and multicloud environments. However, some do so from a predominantly on-premises perspective, others from a predominantly cloud perspective, and others with a blend of both. All of them are quite viable, so buyers need to consider which architecture fits their environment and strategic direction most closely.
Cyber-recovery vendors differentiate themselves in a number of ways. Very often, these involve trade-offs.
Some of the key buying criteria are:
- Complexity: The solutions evaluated in this report range from simple to manage to rather complex. Not surprisingly, the complex solutions may have more capabilities. IT buyers must balance between the desire for simplicity and the need for robust features/functions.
- Breadth of solution: Some vendors seek to supply as many capabilities as possible, while others focus on specific capabilities where they believe they can excel. No vendor can supply everything, and no company needs everything. IT buyers should focus on what they need or can reasonably expect to need in the future.
- Price: While price was not an evaluation criterion in this report, it certainly is an issue for every buyer. Solutions mentioned in this document will vary greatly by price, and finding that balance between cost and solution capabilities is the goal.
- Incumbency: Although this evaluation is conducted as if every reader has a clean slate, the analysts know that’s not true. Some IT buyers will forego some minor “nice to haves” to continue operating with an incumbent vendor. Others will insist on what they deem “best of breed,” regardless of incumbency. Only the buyer can make that trade-off.













 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter


