Synology Security Advisory SA-22:15 GLPI
Concerning multiple vulnerabilities allow remote attackers or remote authenticated users to obtain sensitive information, inject arbitrary web script or HTML or inject SQL command via susceptible version of GLPI.
This is a Press Release edited by StorageNewsletter.com on September 28, 2022 at 2:00 pmSynology, Inc. had published a security advisory concerning software and app in use with its NAS.
Publish time: 2022-09-16 14:27:56 UTC+8
Last updated: 2022-09-16 14:27:56 UTC+8
Severity : Critical
Status : Resolved
Abstract
Multiple vulnerabilities allow remote attackers or remote authenticated users to obtain sensitive information, inject arbitrary web script or HTML or inject SQL command via a susceptible version of GLPI.
Affected products
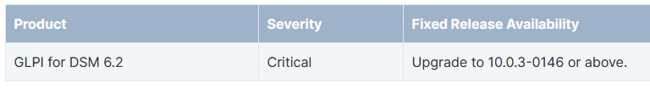 Mitigation
Mitigation
If you need immediate assistance, contact Synology technical support
Detail
-
-
Severity: Critical
-
CVSS3 Base Score: 9.8
-
CVSS3 Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
-
GLPI stands for Gestionnaire Libre de Parc Informatique and is a Free Asset and IT Management Software package, that provides ITIL Service Desk features, licenses tracking and software auditing. Affected versions have been found to be vulnerable to a SQL injection attack which an attacker could leverage to simulate an arbitrary user login. Users are advised to upgrade to version 10.0.3. Users unable to upgrade should disable the
EnableAPI configuration.
login with external token
-
-
-
Severity: Moderate
-
CVSS3 Base Score: 5.3
-
CVSS3 Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N
-
GLPI stands for Gestionnaire Libre de Parc Informatique and is a Free Asset and IT Management Software package, that provides ITIL Service Desk features, licenses tracking and software auditing. It was found that in affected versions there is an exposure of private information defined in setup of GLPI (like smtp or cas hosts). Note that passwords are not exposed. Users are advised to upgrade to version 10.0.3. There are no known workarounds for this issue.
-
-
-
Severity: Moderate
-
CVSS3 Base Score: 8.2
-
CVSS3 Vector: CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:H
-
GLPI stands for Gestionnaire Libre de Parc Informatique and is a Free Asset and IT Management Software package, that provides ITIL Service Desk features, licenses tracking and software auditing. Affected versions were found to not properly neutralize HTML tags in the global search context. Users are advised to upgrade to version 10.0.3 to resolve this issue. Users unable to upgrade should disable global search.
-
-
-
Severity: Moderate
-
CVSS3 Base Score: 7.1
-
CVSS3 Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:L
-
GLPI stands for Gestionnaire Libre de Parc Informatique and is a Free Asset and IT Management Software package, that provides ITIL Service Desk features, licenses tracking and software auditing. Information associated to registration key are not properly escaped in registration key configuration page. They can be used to steal a GLPI administrator cookie. Users are advised to upgrade to 10.0.3. There are no known workarounds for this issue. ### Workarounds Do not use a registration key created by an untrusted person.
-
-
-
Severity: Moderate
-
CVSS3 Base Score: 5.5
-
CVSS3 Vector: CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:L/A:N
-
GLPI stands for Gestionnaire Libre de Parc Informatique and is a Free Asset and IT Management Software package, that provides ITIL Service Desk features, licenses tracking and software auditing. In affected versions request input is not properly validated in the plugin controller and can be used to access low-level API of Plugin class. An attacker can, for instance, alter database data. Attacker must have “General setup” update rights to be able to perform this attack. Users are advised to upgrade to version 10.0.3. Users unable to upgrade should remove the
front/plugin.form.phpscript.
-
-
-
Severity: Low
-
CVSS3 Base Score: 3.5
-
CVSS3 Vector: CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:C/C:L/I:N/A:N
-
GLPI stands for Gestionnaire Libre de Parc Informatique and is a Free Asset and IT Management Software package, that provides ITIL Service Desk features, licenses tracking and software auditing. Usage of RSS feeds or extenal calendar in planning is subject to SSRF exploit. Server-side requests can be used to scan server port or services opened on GLPI server or its private network. Queries responses are not exposed to end-user (blind SSRF). Users are advised to upgrade to version 10.0.3 to resolve this issue. There are no known workarounds.
-
Reference















 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter


