Take Immediate Actions to Stop Qnap NAS From Exposing to Internet and Fight Against Ransomware Together
Statement in response to new type of ransomware named DeadBolt
This is a Press Release edited by StorageNewsletter.com on January 28, 2022 at 2:02 pmQnap Systems, Inc. issued a statement in response to a new type of ransomware named DeadBolt.
DeadBolt has been widely targeting all NAS exposed to the Internet without any protection and encrypting users’ data for Bitcoin ransom. The company urges all Qnap NAS users to follow the security setting instructions below to ensure the security of the firm’s NAS and routers, and immediately update QTS NAS OS to the latest available version.
If your NAS login page is hacked, please try to add ‘/cgi-bin/index.cgi’ to the NAS login URL (e.g. http://nas_ip:8080/cgi-bin/index.cgi), and you should log in accordingly. Contact Qnap technical support for further assistance.
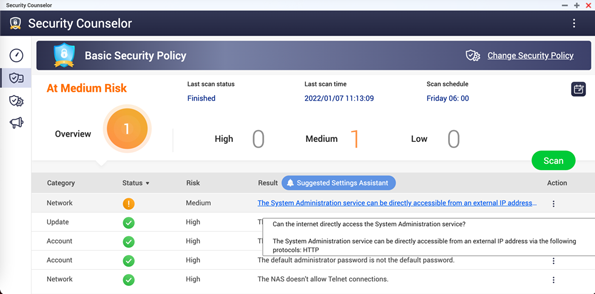
Check whether NAS is exposed the Internet
Open the Security Counselor on your company’s NAS. Your NAS is exposed to the Internet and at high risk if there shows ‘The System Administration service can be directly accessible from an external IP address via the following protocols: HTTP’ on the dashboard.
If your NAS is exposed to the Internet, please follow the instructions below to ensure NAS security:
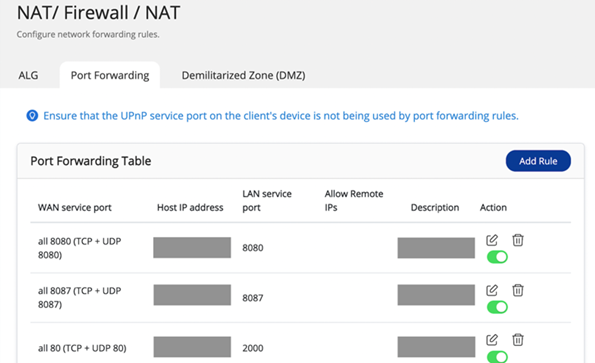
Step 1: Disable the Port Forwarding function of the router
Go to the management interface of your router, check the Virtual Server, NAT or Port Forwarding settings, and disable the port forwarding setting of NAS management service port (port 8080 and 443 by default).
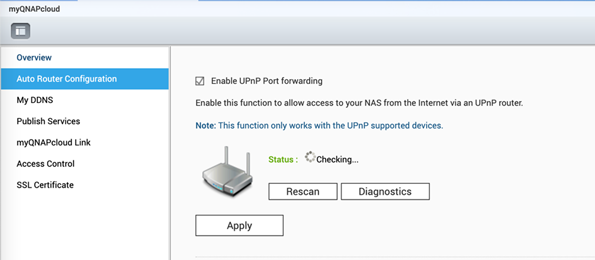
Step 2: Disable the UPnP function of Qnap NAS
Go to myQNAPcloud on the QTS menu, click the ‘Auto Router Configuration’, and unselect ‘Enable UPnP Port forwarding’.















 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter


