Index Engines Advises Greater Scrutiny on Backup Data, Forward Thinking About Ransomware Starts With Backup
CyberSense data analytics product validates integrity inside all files and databases on initial scan.
This is a Press Release edited by StorageNewsletter.com on October 6, 2021 at 1:32 pmGovernment agencies such as the US Federal Bureau of Investigation, the UK’s National Cyber Security Centre), and US Cybersecurity and Infrastructure Security Agency continue to issue warnings on cybersecurity as attacks increase.
Regardless of the vulnerabilities, addressing backup systems is fundamental to reducing the risk of downtime due to ransomware and other cyberattacks, according to experts at Index Engines, Inc., provider of data search, reporting, disposition, and preservation for enterprise needs including IT, legal, and security.
Regular, comprehensive, verified backups are not only key to rapid and reliable recovery, they are also key to identifying that an attack has occurred and knowing the impact. Real-time security sofware is no longer adequate – modern rasomware is sophisticated, and can circumvent basic scans and integrity checks. Highly destructive Ragnar Locker and WastedLocker, to name two, both encrypt data; while others including Conti can shut down backup software entirely.
“Perpetrators of attacks are no longer individual cybercriminals or disgruntled employees, they’ve become high-tech organizations offering Cyberattack-as-a-Service (CAaaS), complete with big budgets and help desks,” said Jim McGann, VP. “Sadly many enterprises are not prepared to go into battle because the very systems that are supposed to keep them safe, backedup and secure, are not as effective as they need to be.”
To provide proper defense, backup and protection products need to perform following added functions:
-
Scan: search backups for signs of attack/compromised data in content (both unstructured files and databases as well as core infrastructure) such as encryption, ransomware, mass deletion, and slow corruption.
-
Alert: immediately notify administrators when signs indicate an attack may have occurred.
-
Diagnose the attack: understand the who, what, where and when of the attack to support recovery.
-
Identify the last good backup: find the last known uncorrupted version so operations return to normal with minimal downtime.
Index Engines further advises organizations that the following tools and practices may be insufficient in the current era of cyberattack, in which criminals are aware of how to cover their tracks.
-
Metadata analysis: as ransomware has become far more advanced, solely examining file metadata for signs of attack is no longer reliable and can be circumvented.
-
Trusting backups: without first validating its integrity; slow attacks can slowly corrupt data, resulting in companies restoring data that still contains ransomware.
-
Trusting security: attacks can hide inside VMs and cached copies of data to circumvent traditional security software, among other methods.
“Rising ransomware is putting pressure on enterprises to have a true cyber recovery plan and not depend on their DR plan,” said McGann. “This includes full analytics, forensic reporting and diagnostics, validating the integrity of the data. Backup needs to be as sophisticated as the cyber criminals and the attack vectors.“
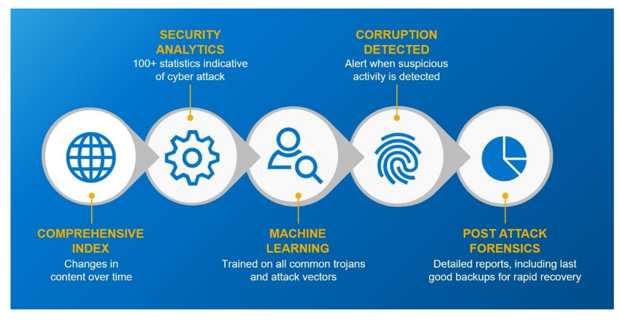
The company‘ software CyberSense is a data analytics product on the market that validates the integrity inside all files and databases on the initial scan. It detects even the most sophisticated corruption that hides inside files, providing 99.5% confidence in alerting an attack occurred. This is far more reliable than metadata-only scans or sending sensitive content to the cloud for analysis. CyberSense ML analysis compares data as it changes over time to detect suspicious behavior and cyber corruption.
The software, available via Dell Technologies, Inc.’s PowerProtect Cyber Recovery vault, provides post-attack reports and diagnostic details to assist recovery. In most cases, CyberSense users will reduce their recovery time from weeks and months to hours.














 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter


