Dispersive Technologies Adds Another Defense Layer to Storage Platform
Software tool that defeats data theft and malware insertion and prevents unauthorized manipulation of stored data
This is a Press Release edited by StorageNewsletter.com on March 10, 2016 at 2:44 pmDispersive Technologies, Inc. announced a authentication feature for its storage platform.
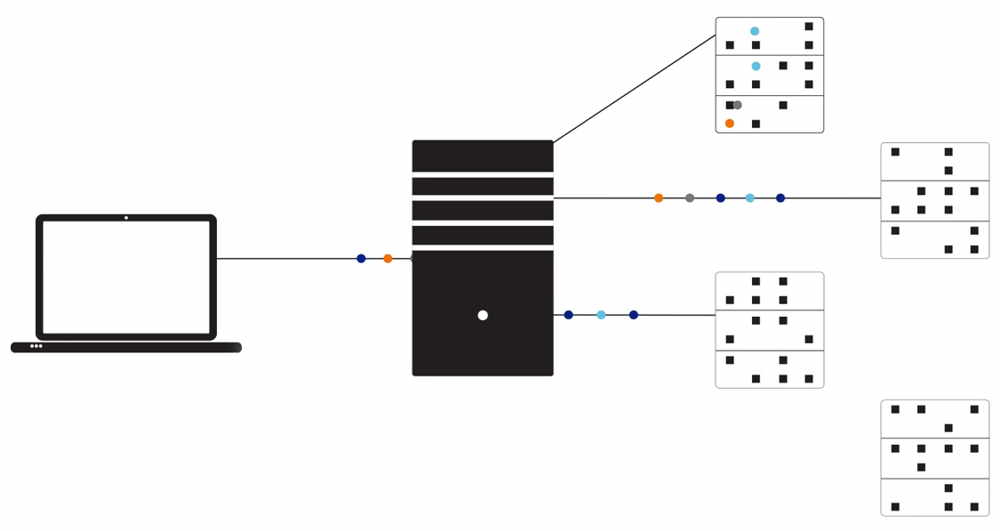 Dispersive Storage is a software tool that effectively defeats data theft and malware insertion and prevents unauthorized manipulation of stored data by dividing it into small blocks, spreading these blocks across geographically disparate areas, and periodically shuffling their locations.
Dispersive Storage is a software tool that effectively defeats data theft and malware insertion and prevents unauthorized manipulation of stored data by dividing it into small blocks, spreading these blocks across geographically disparate areas, and periodically shuffling their locations.
The feature will add another layer of defense to the platform by providing dynamic authentication capabilities. Dispersive Storage will remove random bytes from storage locations and use them to form a dynamic key that changes with each shuffling. It including its authentication feature, will be available later this year.
“This feature introduces a novel approach to combat the ever present and increasingly aggressive and sophisticated cyber threat,” said Robert W. Twitchell, Jr., president and CEO, Dispersive. “It also demonstrates our holistic, from-the-ground up approach o networking. When companies use Dispersive Storage with Dispersive Virtualized Networks, they truly enjoy security without compromise for their data-at-rest and data-in-motion.“
Firm’s Virtualized Networks (VNs) use any single or combination of physical connections to the Internet, commodity hardware and Dispersive software to deliver data with greater speed, tighter security and more reliability than private networks. The combination of this software platform with Dispersive Storage creates the Dispersive SDN, a software-defined network that improves the network performance for everything from SCADA and IoT devices to mobile workforce and high-end servers in the cloud.
“Many companies are used to security solutions with overhead penalties,” Twitchell added. “They just assume network security and performance are mutually exclusive. Our solutions prove it’s not an either-or situation. Speed, security and reliability can co-exist. And because our software works with all existing infrastructure, runs on commodity hardware, and enables the use of lower-cost bandwidth, these improvements in security and performance are typically achieved at a lower total cost.“














 Subscribe to our free daily newsletter
Subscribe to our free daily newsletter


